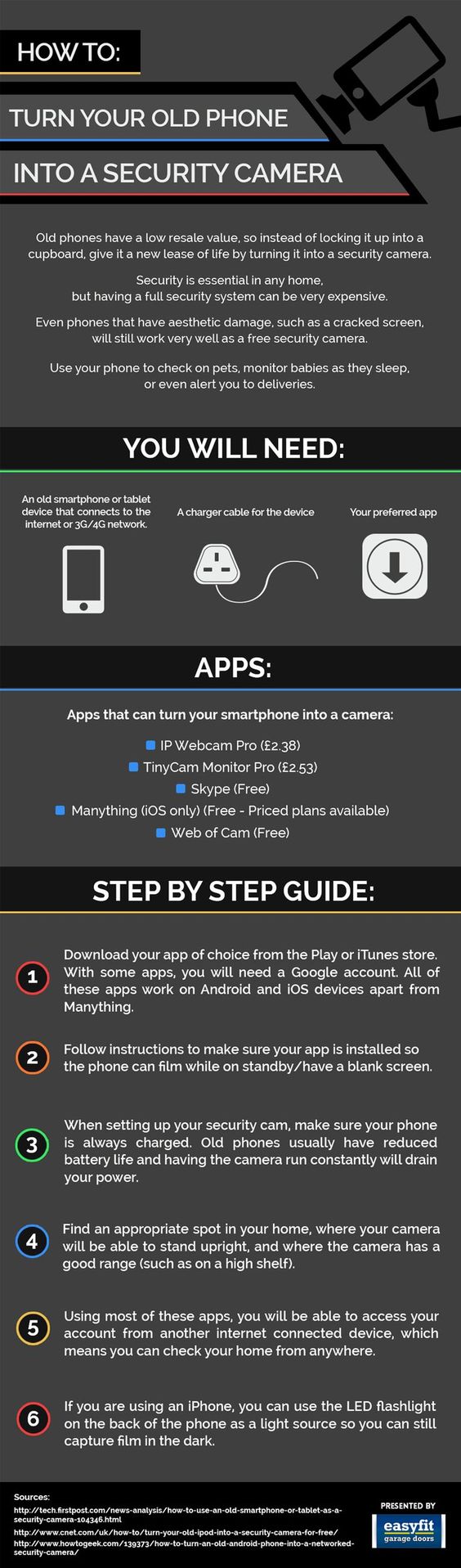
Cybersecurity researchers at Armis Labs have released information about a new attack vector called BlueBorne. This exploit has the potential to put millions of devices running Windows, Linux, Android or iOS operating systems at risk.
Cybersecurity researchers at Armis Labs have released information about a new attack vector called BlueBorne. This exploit has the potential to put millions of devices running Windows, Linux, Android or iOS operating systems at risk.
This exploit allows attackers to connect over the Bluetooth radio system with having to first pair the two Bluetooth enabled devices. Once installed, the attacker has full control of ...
Continue Reading →SEP