A guest infographic from Chicago area managed service provider MXOTech. I recommend clicking thorough the link so you can read the complete article.
Continue Reading →FEB
A guest infographic from Chicago area managed service provider MXOTech. I recommend clicking thorough the link so you can read the complete article.
Continue Reading → The Corp.com domain is for sale, and depending on who ends up owning it, this could be catastrophic for companies that use Windows domains and Active Directory. It basically is Microsoft’s fault (of course), except it is not. The problem is that many admins who were setting up Active Directory domains for their company followed the directions a little too exactly. In ...
The Corp.com domain is for sale, and depending on who ends up owning it, this could be catastrophic for companies that use Windows domains and Active Directory. It basically is Microsoft’s fault (of course), except it is not. The problem is that many admins who were setting up Active Directory domains for their company followed the directions a little too exactly. In ...
 Insider threats, the risks and dangers caused by malicious or careless acts performed by your own employees, contractors, and trusted vendors is perhaps the most difficult cyber attack to detect and defend. What happens when a member of your own IT department turns to the dark side?
Insider threats, the risks and dangers caused by malicious or careless acts performed by your own employees, contractors, and trusted vendors is perhaps the most difficult cyber attack to detect and defend. What happens when a member of your own IT department turns to the dark side?
Between 2015 and 2019, IT executive Hicham Kabbaj scammed his employer out of $6 million dollars for servers, other products, and installation services by ...
Continue Reading →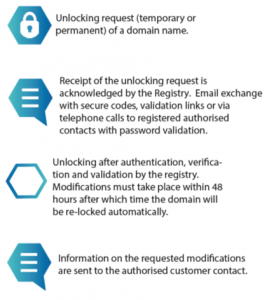 How can you have a domain lock or client transfer prohibited, and still lose your domain name to attackers? Domain lock was invented to prevent unauthorized parties from stealing your domain name. As reported by Brian Krebs on January 24, 2020, that happened to a well regarded service that helps Web sites detect and block fraud. They had a domain lock but ...
How can you have a domain lock or client transfer prohibited, and still lose your domain name to attackers? Domain lock was invented to prevent unauthorized parties from stealing your domain name. As reported by Brian Krebs on January 24, 2020, that happened to a well regarded service that helps Web sites detect and block fraud. They had a domain lock but ...
 Today I am running a guest post by Panda Security, courtesy of my friends at Siege Media. As you may have heard, 2019 was the year of ransomware. The target? The public sector. With variations such as Cryptolocker, German Wiper and Robinhood, there was a shocking number of government ransomware attacks this past year. ...
Today I am running a guest post by Panda Security, courtesy of my friends at Siege Media. As you may have heard, 2019 was the year of ransomware. The target? The public sector. With variations such as Cryptolocker, German Wiper and Robinhood, there was a shocking number of government ransomware attacks this past year. ...
 Today I share an infographic provided by repeat guest poster Siege Media. The Internet of Things is full of cool new devices that connect to the network and Internet, and can be used from distant locations. But if used without proper security controls, these smart devices can provide an easy remote entry point for an attacker.
Today I share an infographic provided by repeat guest poster Siege Media. The Internet of Things is full of cool new devices that connect to the network and Internet, and can be used from distant locations. But if used without proper security controls, these smart devices can provide an easy remote entry point for an attacker.
I have not republished the excellent article that was part of the original post,
Continue Reading → Cyber-criminals, state-sponsored cyber warriors, cyber-terrorists, and law enforcement cyber divisions all face the same choice when launching a campaign against a person, company, or governmental agency – do I start with a hard target or a soft target? Modern networks, even for small businesses and individuals, are usually tough to breach from the Internet side. Networks are hardened with layers of defensive hardware and software that make a direct attack ...
Cyber-criminals, state-sponsored cyber warriors, cyber-terrorists, and law enforcement cyber divisions all face the same choice when launching a campaign against a person, company, or governmental agency – do I start with a hard target or a soft target? Modern networks, even for small businesses and individuals, are usually tough to breach from the Internet side. Networks are hardened with layers of defensive hardware and software that make a direct attack ...
 Can a cyber attack force you to go out of business? Ransomware attacks are causing small business targets of these attacks to close their doors, even after they paid the attackers for the decryption key. The financial losses and impacts of the attack are just not survivable for some businesses..
Can a cyber attack force you to go out of business? Ransomware attacks are causing small business targets of these attacks to close their doors, even after they paid the attackers for the decryption key. The financial losses and impacts of the attack are just not survivable for some businesses..
In 2019, we saw a dramatic increase in both ...
Continue Reading → Using Bluetooth to connect devices to your laptop is convenient but also risky. Discover what those risks are and how to minimize them.
Using Bluetooth to connect devices to your laptop is convenient but also risky. Discover what those risks are and how to minimize them.Many laptops come with Bluetooth connectivity. Thanks to this wireless technology, you can easily connect a keyboard, mouse, headset, or other peripheral to your laptop. You can even use it to send files to a printer ...
Continue Reading →![]() Is there a way to maintain privacy online, and defeat tracking without resorting to extreme measures? We have written articles recently about the most private browsers, but using them requires changing habits and abandoning web browsers that you are already familiar with.
Is there a way to maintain privacy online, and defeat tracking without resorting to extreme measures? We have written articles recently about the most private browsers, but using them requires changing habits and abandoning web browsers that you are already familiar with.
I came across this graphic on Pinterest, and thought it was worth sharing. It shows some ...
Continue Reading →