 This is a special report on the emerging situation in the Ukraine, the NATO Alliance, and attacks by Russian Federation cyber-operations against the West.
This is a special report on the emerging situation in the Ukraine, the NATO Alliance, and attacks by Russian Federation cyber-operations against the West.
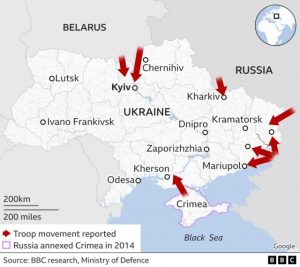
I find it ironic that Putin claims to be invading Ukraine to rid it of Nazis. Everything he has done in the last decade to reclaim lands in Belarus, Georgia, the Crimea, and eastern Ukraine is straight out of Hitler’s playbook. Hitler systematically annexed parts of the “German homeland” starting in the Rhineland, then the Sudetenland, the Austrian Anschluss, and then the invasion and partition of Poland. Following up with Blitzkrieg tactics against Belgium, Holland, and France. Japan saw the US as weak. American refusal to join the war in Europe lead directly to the Japanese attack on Pearl Harbor. It’s all happening again, just the players have changed.
Putin has modernized warfare by combining traditional kinetic warfare with cyber war tactics. Putin is more like Hitler than any ruler since World War II. Russia, China, Iran, and North Korean are the new Axis Powers. If the west does not stop him now, we will see the fall of Poland and the Baltic States, and perhaps Romania and Hungary. In the Asian theatre we could expect China to take Taiwan, and perhaps expand into other Asian countries like Korea and Japan. If we are not strong now, this could easily devolve into World War III.
Here are advisories on how the cyber war is already being felt in the west. We are presently being attacked by Russia, China, Iran, and North Korea. This is not hypothetical, it is happening now!
Timeline of Russian Cyber Attacks in a PDF document
CISA Releases Advisory on Destructive Malware Targeting Organizations in Ukraine
Original release date: February 26, 2022
CISA and the Federal Bureau of Investigation have released an advisory on destructive malware targeting organizations in Ukraine. The advisory also provides recommendations and strategies to prepare for and respond to destructive malware.
Additionally, CISA has created a new Shields Up Technical Guidance webpage that details other malicious cyber activity affecting Ukraine. The webpage includes technical resources from partners to assist organizations against these threats.
CISA recommends organizations review Destructive Malware Targeting Organizations in Ukraine and Shields Up Technical Guidance webpage for more information.
New Sandworm Malware Cyclops Blink Replaces VPNFilter
Original release date: February 23, 2022
The United Kingdom’s National Cyber Security Centre, CISA, the National Security Agency, and the Federal Bureau of Investigation have released a joint Cybersecurity Advisory (CSA) reporting that the malicious cyber actor known as Sandworm or Voodoo Bear is using new malware, referred to as Cyclops Blink. Cyclops Blink appears to be a replacement framework for the VPNFilter malware exposed in 2018, which exploited network devices, primarily small office/home office routers and network-attached storage devices.
CISA encourages users and administrators to review joint CSA: New Sandworm Malware Cyclops Blink Replaces VPNFilter for additional technical details and mitigations.
CISA Insights: Foreign Influence Operations Targeting Critical Infrastructure
Original release date: February 18, 2022
CISA has released CISA Insights: Preparing for and Mitigating Foreign Influence Operations Targeting Critical Infrastructure, which provides proactive steps organizations can take to assess and mitigate risks from information manipulation. Malicious actors may use tactics—such as misinformation, disinformation, and malinformation—to shape public opinion, undermine trust, and amplify division, which can lead to impacts to critical functions and services across multiple sectors.
Current social factors—including heightened polarization and the ongoing global pandemic—increase the risk and potency of influence operations to U.S. critical infrastructure. CISA encourages leaders at all organizations to review the CISA Insights and follow the guidance to assess risk and increase resilience
Spear Phishing Attacks Target Organizations in Ukraine, Payloads Include the Document Stealer OutSteel and the Downloader SaintBot
On Feb. 1, 2022, Unit 42 observed an attack targeting an energy organization in Ukraine. CERT-UA publicly attributed the attack to a threat group they track as UAC-0056. The targeted attack involved a spear phishing email sent to an employee of the organization, which used a social engineering theme that suggested the individual had committed a crime. The email had a Word document attached that contained a malicious JavaScript file that would download and install a payload known as SaintBot (a downloader) and OutSteel (a document stealer). Unit 42 discovered that this attack was just one example of a larger campaign dating back to at least March 2021, when Unit 42 saw the threat group target a Western government entity in Ukraine, as well as several Ukrainian government organizations.
Anonymous Attacks Russia
The Anonymous collective declares cyberwar against the Russian government.
Around 30 minutes later, they announced that they had taken down the website of the Kremlin-backed TV channel RT, which broadcasts in Britain and has been heavily criticized for its coverage.
Cyber war is a game anyone can play. This is going to be interesting.
Share
FEB




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com