 On of the more hopeful presentations from the Cyber Security Summit was presented by Tony Sager from the Center for Internet Security. Titled “Making Best Practices Common Practices: The CIS Controls,” Tony provided us with a road map for implementing secure practices in our networks.
On of the more hopeful presentations from the Cyber Security Summit was presented by Tony Sager from the Center for Internet Security. Titled “Making Best Practices Common Practices: The CIS Controls,” Tony provided us with a road map for implementing secure practices in our networks.
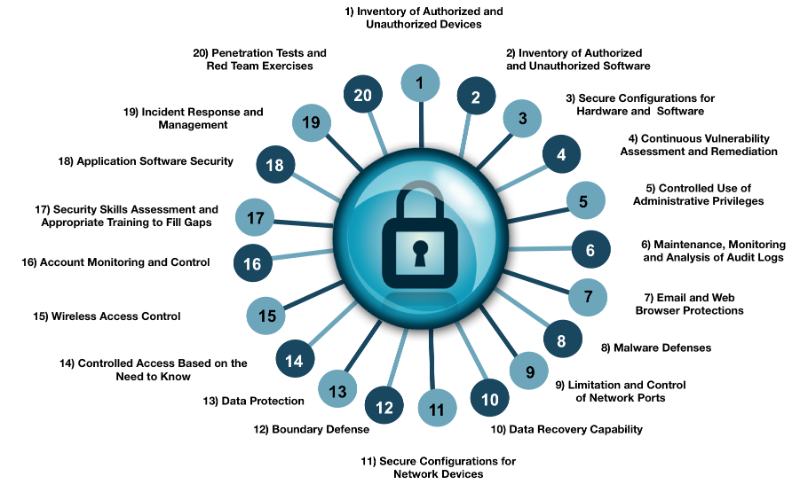
There are 20 CIS controls. Tony said that implementing the first 5 (20%) would reduce your risk by 80%. You can check out the chart below for all twenty. If you are working the NIST-CSF in your organization, the CIS Controls can help you prioritize and streamline your implementation.
The first 5 controls are:
- Inventory of authorized and unauthorized devices – most businesses have no real idea of what is attached to their network. This solves that problem.
- Inventory of authorized and unauthorized software.
- Secure configurations for hardware and software on mobile devices, laptops, workstations, and servers.
- Continuous vulnerability assessment and remediation – when we perform follow-up vulnerability scans, we always find vulnerabilities that weren’t on the previous scan. That’s because new vulnerabilities are discovered all the time.
- Controlled use of administrative privileges – giving every user local administrative privileges is a recipe for disaster. Anyone logged onto a system, including an attacker, has full rights for installing software and making other critical system changes
Here are the rest. More complete information can be found on the Center for Internet Security website.
Share
NOV




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com