In the last month there have been several notable web site breaches where the cyber-thieves made off with databases full of user credentials. New additions to the list (Target, Michael’s, Neiman Marcus) now include PF Chang’s, Goodwill Industries, Jimmy John’s, eBay, and most recently, CNet. I have had to change my eBay password, which means I changed my PayPal password as an added safety measure. I also changed the password on my CNet account. CNet is a technology publisher, and the account credentials are not terribly significant, but because this is a relatively trivial account, I used a short easy password that I also used on other similar trivial accounts. So this ended up being a more involved task, since I had to change the password on several other sites. This shows the problem with using the same password on several web sites. If you get hacked in one place, you are basically hacked everyplace.
How Passwords Are Cracked
- User ID and password information is stored in an encrypted form.
- Special computers or a large botnet will run software against the encryption, using lists of dictionary words (Dictionary Attack), words with some character substitution (Hybrid Attack) or just try every possible combination (Brute Force Attack)
- Once broken, lists are created with the user ID, the encrypted password, and the cracked or clear text password. These lists are called Rainbow tables.
- With Rainbow Tables, you just need to compare the encrypted passwords on a new target server, with the encrypted passwords on the Rainbow Table to get the clear text password.
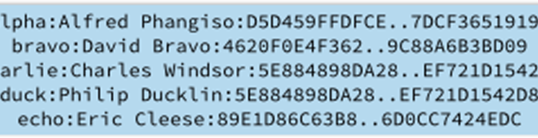
In the sample Rainbow Table shown below, we have in the first column the solved clear text password (alpha), the user name (Alfred Phangiso) and the password’s encrypted hash. When a new set of user names and encrypted password hashes are stolen from a web server, instead of having to use a time consuming brute force decryption method, instead I can just use software that compares my hashed passwords to the hashes in my Rainbow Table. This is much faster than cracking the password. If I get the hashes to match, the table provides the clear text password.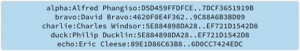
With the rise in the use of Rainbow Tables by cyber-criminals, these hacked credentials end up in lists that are sold on the Dark Web, and these credentials are tried on other web sites, on the fairly good chance that some of these passwords have been used more than once by the same person on different web sites. If this is you, mend your ways, or at least understand that you are basically at the same risk as having no password.
The really bad news – the day of the password is very nearly over. What this means is that the tools the cyber-criminals are using are making the password an insecure form of security. Many security researchers are working on security solutions that either augment passwords, such as two-factor authentication (2FA),or preplacing them completely with proximity or biometric authentication schemes. But that is the subject of another post.
AUG




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com