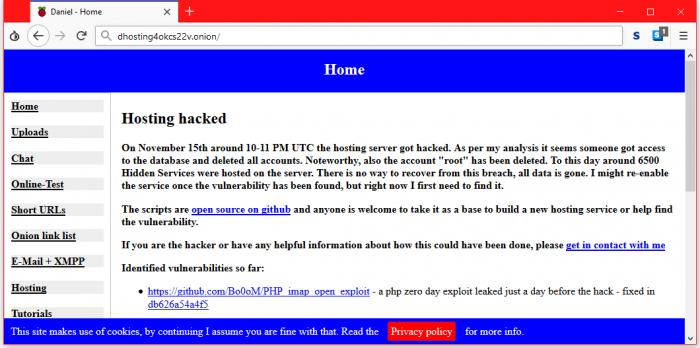
I recently started spending time in the Dark Web, learning how to use a VPN and the TOR browser to navigate the hidden services to be found there. I also have been presenting a “Tour of the Dark Web” to the public in a variety of business groups. I find the Dark Web to be a fascinating place, and so far the response from people attending my seminar indicates that I am not the only one. One of the problems with finding sites on the Dark Web is that there are no search engines that work there. Information about hidden sites and services are kept in lists such as the Hidden Wiki. These lists are often inaccurate and out of date, since sites go up without notice, and come down the same way. Then there is the sudden loss of 6500 Dark Web sites when Daniel’s Hosting was breached on November 15.
Last week a popular Dark Web hosting service, Daniel’s Hosting, was breached by as of yet unknown attackers, and the entire contents of the hosting platform were stolen and/or erased. This took down about 30% of the hidden services across the TOR network, representing about 6500 sites, and over 6 million documents. The carnage included:
- All of the user account information, including the “root” account.
- 5000 or more English language sites.
- 54 Russian language sites
- 450 hacking and malware development sites
- 300 forums
- 150 chat rooms
- 135 drug markets
- 109 counterfeit services
- 50 sites dealing stolen credit cards
- 20 sites dealing in weapons
- 700 sites that were used for unknown purposes.
So far this is no one has taken credit for this attack, but speculation points to a couple of possibilities. The first is a Russian hacker collective who recently published technical details of the PHP imap_open() vulnerability, which was apparently used in this attack. The second possibility is that this server has taken down by a law enforcement agency. There was a DDoS attack the precede the breach, similar to other law enforcement takedowns. There were a few child pornography chat rooms using Daniel’s Hosting. It is possible that Daniel Winzen, the owner, has been arrested, and his recent posts about the issue are really coming from law enforcement.
Supposedly the service will be back in December, once he has had a chance to secure his server. By design, the site kept no backups, so restoring the lost sites will fall on the individual site owners.
ShareDEC




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com