 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: RingCentral Voicemail Phish
Chef’s Special: KONNI Malware Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
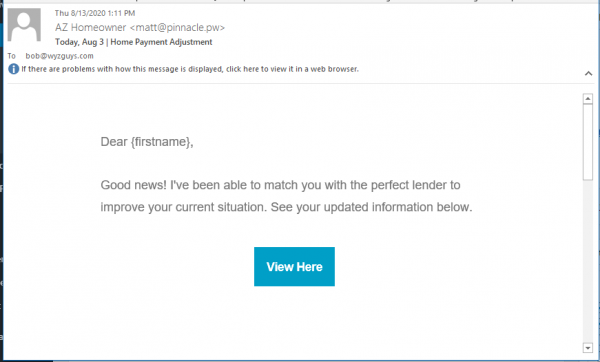
Pinnacle Mortgage Spam
Be careful where you sign up. Even though I gave a false email address on their web form when I was tracking down an email from Pinnacle a few weeks ago, because I used the provided link, the encoding identified the email address they sent it to, and my legitimate email account was registered. I keep getting mortgage related offers from these guys. The Dear {firstname} greeting is a nice touch. Today I noticed a MailChimp logo at the bottom of the email, so I gave a stab at unsubscribing. We’ll let you know if it works or not.
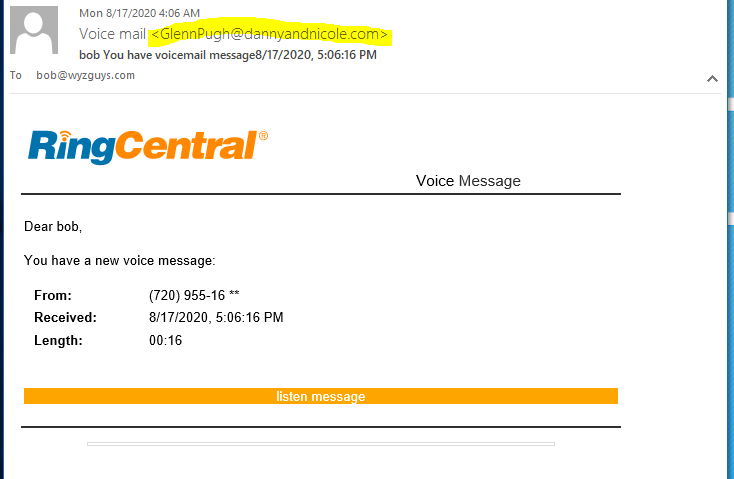
RingCentral Voicemail Phish
This is just ANOTHER attempt to get my email credentials. Lets see how it works.
The Listen Message link resolves to https://rengcall.firebaseapp.com/bob-bob/bob#bob@wyzguys.com. The landing page is below. I was disappointed that they changed logos and trade dress in the middle of the scam.
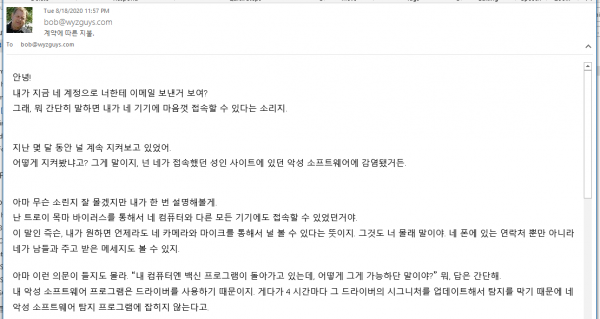
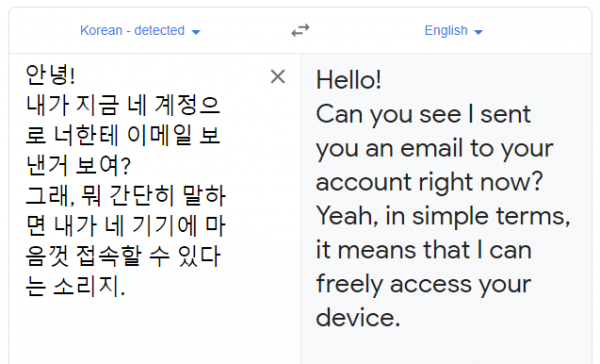
Korean Extortion Phish
Most of you would just delete an email in a foreign language, and that is a good plan. But I received an email in Korean and was curious what email contained. It was just a “we’ve been videoing your naughty behavior” Bitcoin extortion scams. Here’s what it looked like, courtesy of Google Translate.
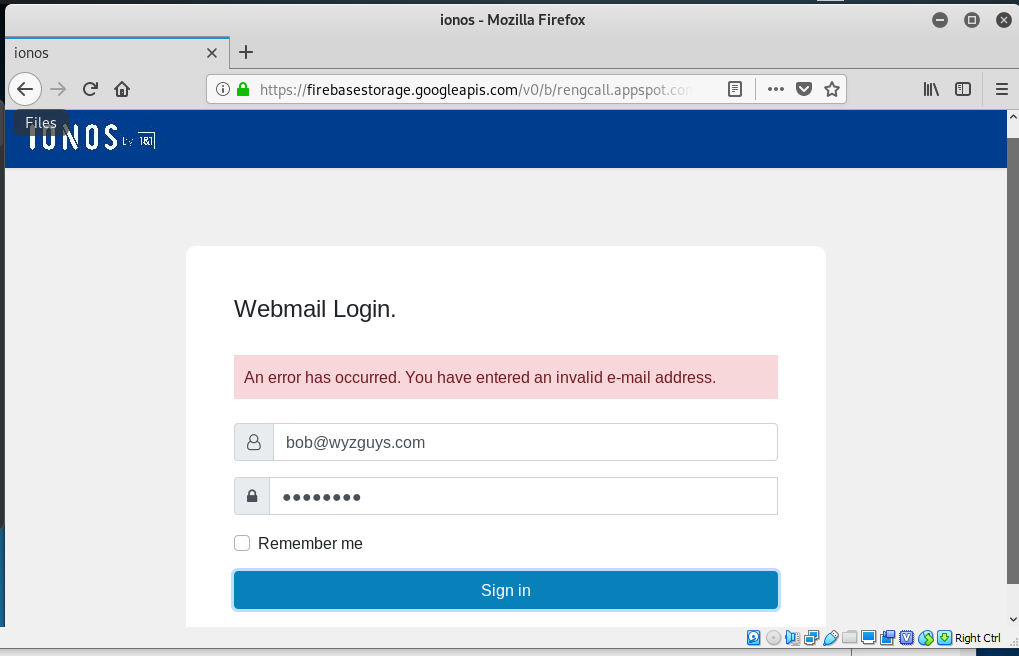
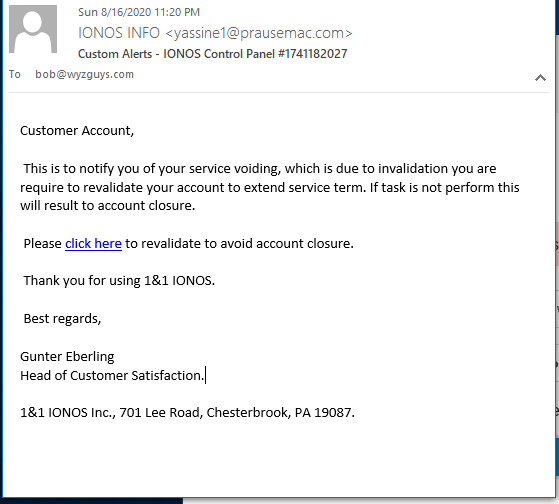
A Really Bad IONOS Phish
Maybe if you are going to be a scammer, you should learn how to run a spelling and grammar checking program. Pretty sure no one would fall for this, it is a classic case of poor English grammar in a phish.
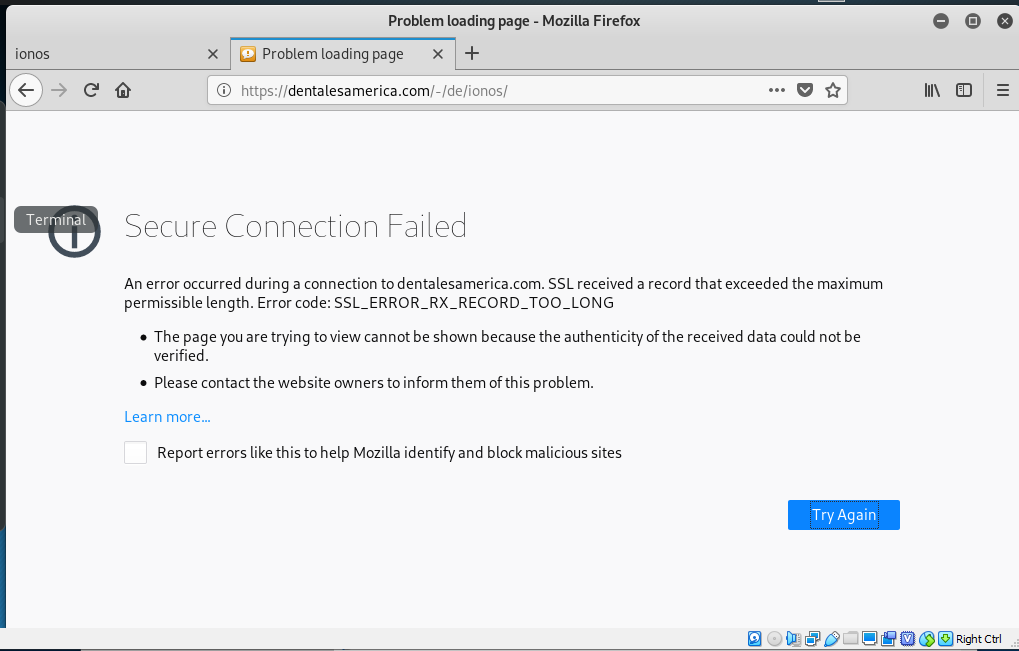
The link resolved to https://t.co/mdgOlHoq0K?amp=1?http://www.otto.de/917411820274?http://www.google.com/zabi, and was redirected to a page on dentalesamerican.com. I just played this through for laughs, and the page link was already broken.
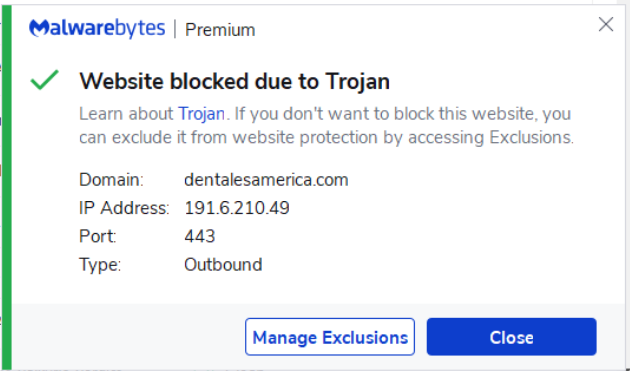
Malwarebytes sure didn’t like the link destination,though.
AA20-227A: Phishing Emails Used to Deploy KONNI Malware
Original release date: August 14, 2020
Summary
This Alert uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework.
The Cybersecurity and Infrastructure Security Agency (CISA) has observed cyber actors using emails containing a Microsoft Word document with a malicious Visual Basic Application (VBA) macro code to deploy KONNI malware. KONNI is a remote administration tool (RAT) used by malicious cyber actors to steal files, capture keystrokes, take screenshots, and execute arbitrary code on infected hosts.
Share
AUG




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com