 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Google Privacy Check-up
Chef’s Special: Blocked Message WyzMail Spoofing Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox.
Take the Google Privacy Checkup
One of the problems with becoming cybersecurity-aware is that sometimes we suspect legitimate and helpful emails from being a phish. I got this Google Privacy Check-up email, and I am featuring it in the Phish Fry as something you should actually do. The link in the title Take the Google Privacy Checkup is safe. Even though I was certain about the validity of this email, I still ran the link through VirusTotal and opened the link in my Linux virtual machine first. Here is the email:
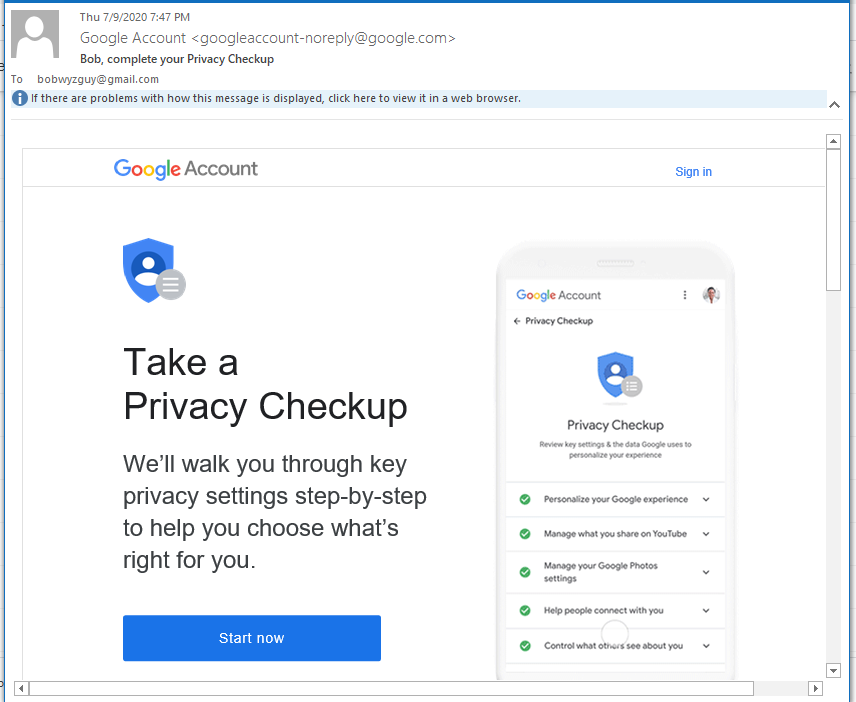
This is the original email. The sender email is legitimate and the receiver email is my gmail address.
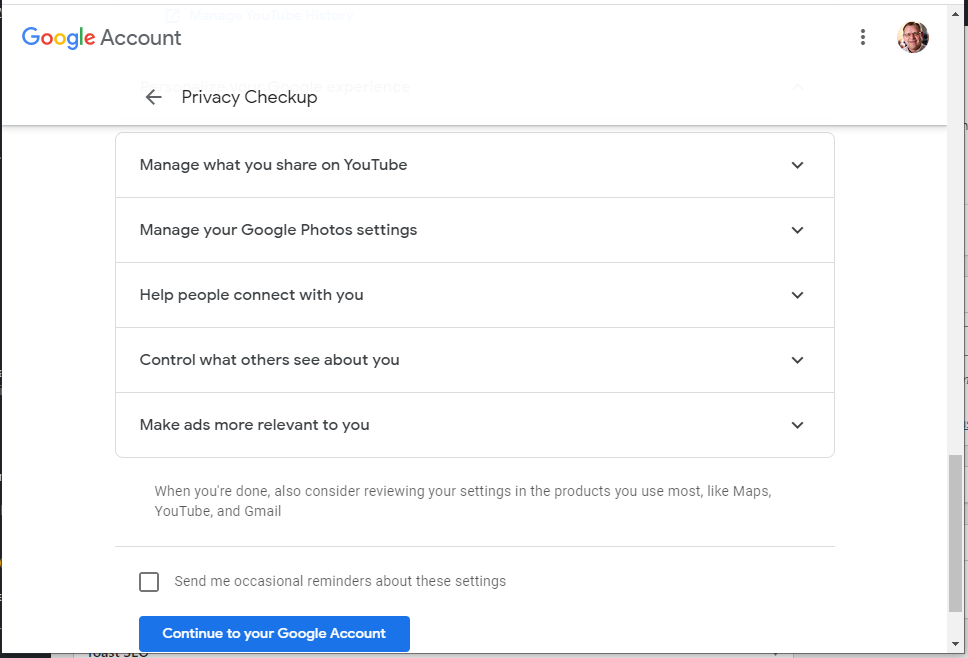
The privacy settings you can control include:
Web & App Activity
Google is saving your activity on Google sites and apps, including searches and associated info like location, in your Google Account. Google is also saving activity such as which apps you use, your Chrome history, and which sites you visit on the web.
This helps Google to give you faster results by auto-completing searches, as well as smarter and more useful experiences in Maps, Assistant, and other Google services.
Location History
Google creates a private map of where you go with your signed-in devices even when you aren’t using a specific Google service. This map is only visible to you.
This gives you improved map searches and commute routes, as well as helping you to rediscover the places you’ve been and the routes you’ve traveled.
YouTube History
I recommend checking your Google account settings at last annually. Might as well check your Microsoft account and Apple account while you are at it.
Blocked Message WyzMail Spoofing Phish
WyzMail.com is one of my registered domains. This phishing example will show how your won domain name can be spoofed. Today (7-14-2020) I received an email with the subject Blocked Incoming Messages. The sender address was a mismatch (mcdean.site), and a quick visit to that domain spawned a security warning by Firefox on my Kali VM.
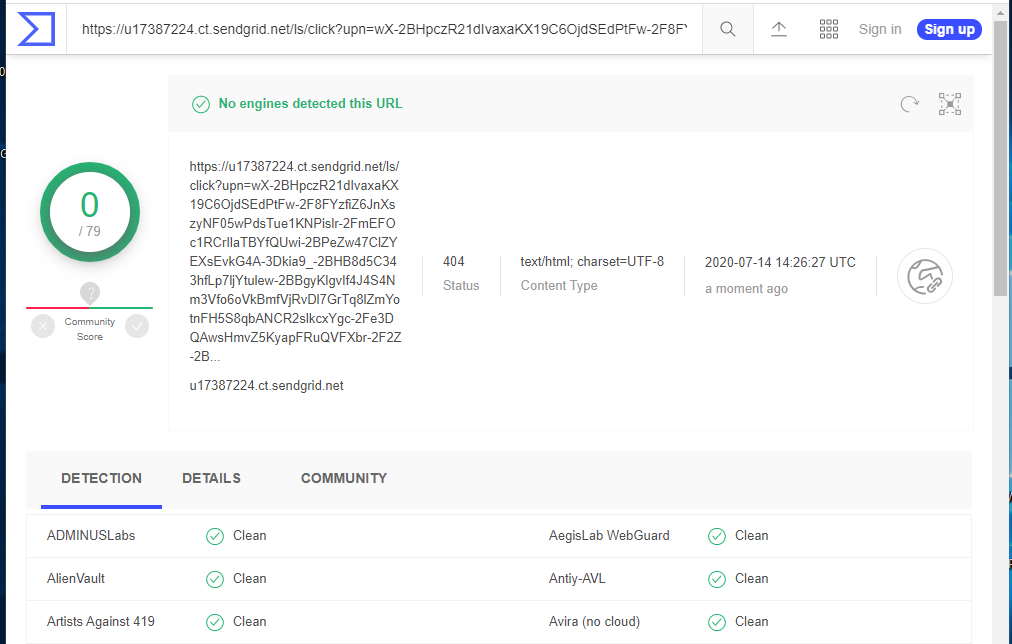
The button an link resolved to a lengthy URL that I have truncated for simplicity. (https://u17387224.ct.sendgrid.net/ls/click?) Virustotal gave this URL a clean bill of health, but this was redirected to https://eweb.avitsystensinc.com/en/web/Wyzmail-85752/access.php?Session=ID… When I checked this URL with VirusTotal, it came up as a phishing and spam site.
I am seeing this a lot lately – a URL that checks out as clean being redirected to one that is dirty. So taking my earlier advice about checking links on VirusTotal is not going to help you keep safe. You are going to have to assume all links are dangerous.
See below:
Problems with the sender email domain mcdean.site security certificate
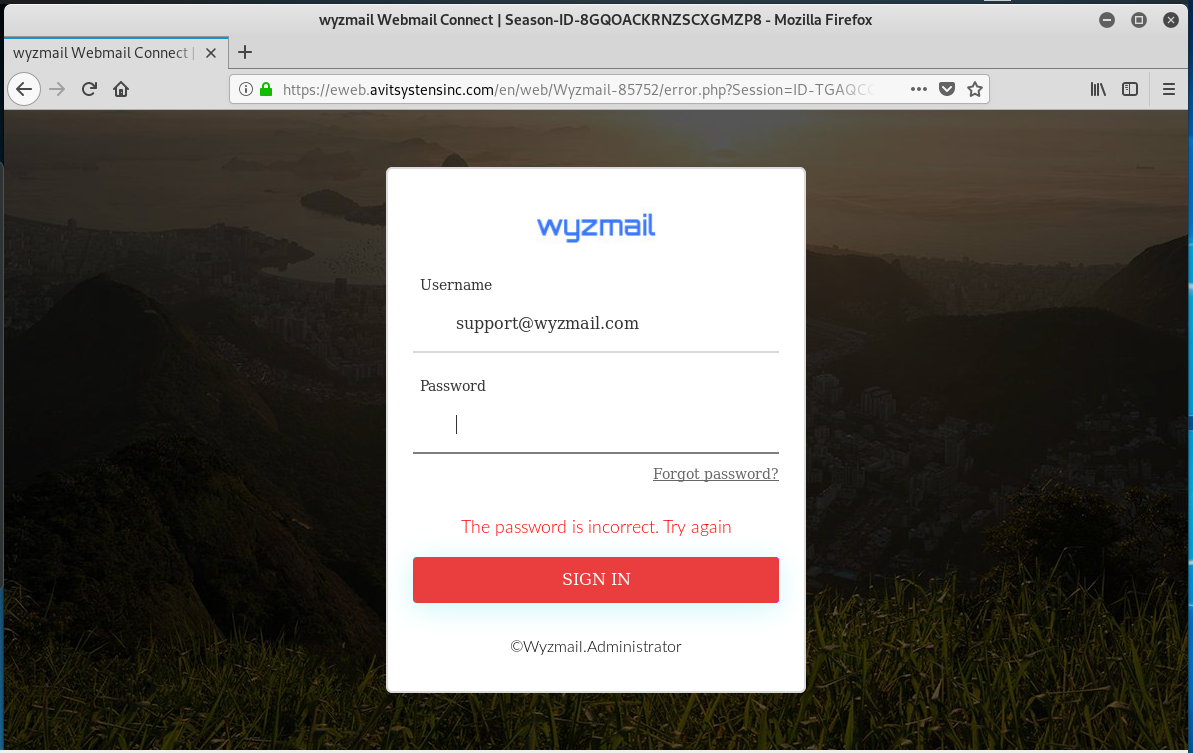
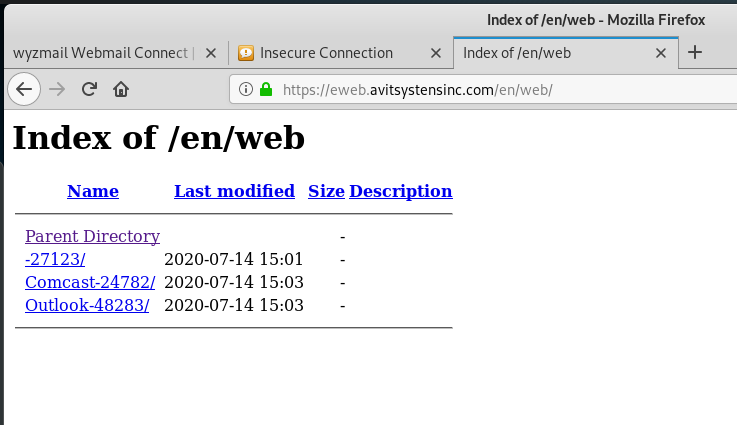
I continued on through the links to the landing page. Here we see the WyzMail domain spoofed for the first time. The “logo” is nothing like my actual logo, but WyzMail clients may be fooled enough to enter their password in the form. When I did that, I got a password error message, but the scammers did get the “FakePassword” that I entered. I tested the URL without the Session ID hoping to find another victim of a website hijacking. But this website is dedicated to this phishing scam, leaving off my session ID got me the same credential stealing page, but without the WyzMail logo and pre-populated email address. See below
When I tried to enter the shorten address a second time, I was directed to the site’s index page. I shouldn’t really be permitted to see this, but what it shows is that this exploit is very young, launched today. And evidently Comcast and Outlook email users are also being targeted.
This is a pretty interesting exploit, and I had fun dissecting it and sharing it with my followers. The take-away? A clean bill of health from VirusTotal is proof of nothing. If you insist on clicking through, watch out for URL redirection.
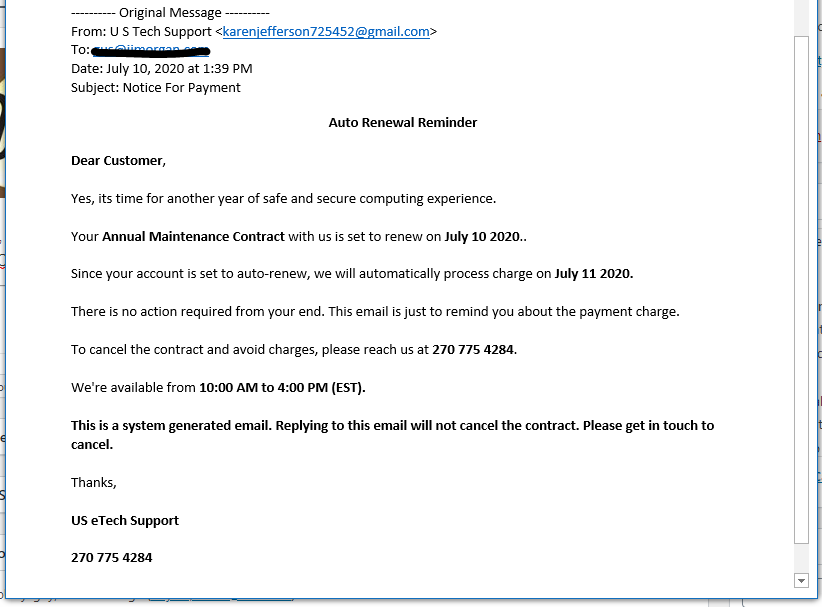
Fake Tech Support Email and Telephone Combo Scam
A nice contribution from a client. This email combines the phish with the typical telephone social engineering scam. A call to the phone number connected me with a customer service rep with a distinct Indian accent. Why is it always someone from India? Anyway, the phone call progressed as expected, and renewal was going to be $299.99. $300 must be some kind of big money in India, because whatever the scam, that is always the price. You can ignore emails like this unless you need a laugh.
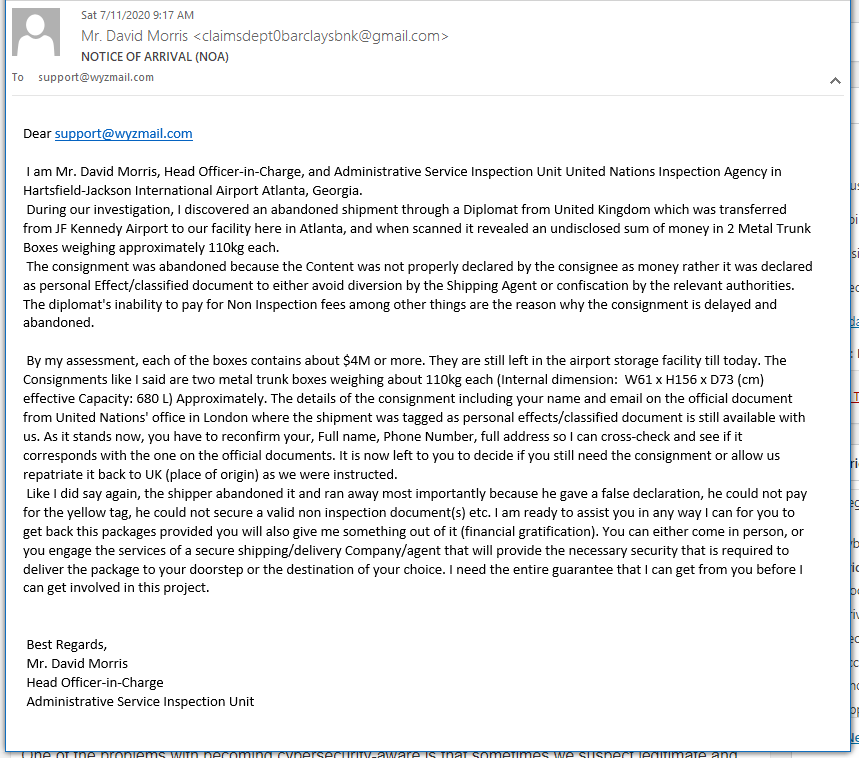
Advance Fee Fraud is Alive and Well
I got this email today, Nothing to click on and no phone number to call, so I just sent a reply. Still waiting for a response. I did find it interesting the at return email address was different than the apparent sender’s email address.
Notice the different email addresses for “David Morris.”
Phishing, Vishing & Smishing
A video from the National Cybersecurity Alliance (45 minutes)
You may have heard of the term phishing, but do you really know what it means and how you can protect yourself from this type of cyber threat? What about other threats, such as smishing and vishing? During this webinar, speakers from the National Cyber Security Alliance, Cofense, and Trend Micro break down these terms and outline steps you can take to protect yourself from cyber criminals.
Office 365 Phishing Attacks Now Use Fake Zoom Suspension Alerts
Microsoft Office 365 users are targeted by a new phishing campaign using fake Zoom notifications to warn those who work in corporate environments that their Zoom accounts have been suspended, with the end goal of stealing Office 365 logins. More…
“SLicK” New Phishing Attack Targets 200M+ Microsoft 365 Accounts Via Malicious Excel .SLK Files to Bypass Security
From KnowB4 – Using an old (but supported) .SLK Excel file extension, attackers can bypass both Exchange Online Protection and Advanced Threat Protection to run malicious macros. Security researchers at Avanan have discovered a new attack method where cybercriminals send phishing emails that contain what appears to be an Excel spreadsheet. The file is actually an SLK file – a “Symbolic Link” Excel file used to transfer data between spreadsheet programs and other databases – to host a macro that launches an MSI script.
There are a few aspects of this attack that make it particularly worrisome for organizations using Microsoft 365:
- The phishing emails are targeted and are written in an organization-specific, and sometimes user-specific manner
- It appears to be an Excel file (because it is) which is a known file format
- Most Office users know not to enable macros (or have them administratively disabled) and, therefore, think it’s fine to open an Excel spreadsheet (“It can’t hurt me, right?”)
- The filetype currently bypasses all Microsoft 365 security
- Windows “Protected View” does not apply to SLK files, so the file is NOT opened in read-only mode, leaving the user vulnerable to attack
- The call to run the Microsoft Installer runs in quiet mode and installs a hacked version of NetSupport remote control
It’s devious and VERY dangerous. Users that fall for the initial social engineering scam (again, one that is written specifically for the org and user targeted) will find themselves a victim upon opening the attachment.
Organizations need to first configure their Microsoft 365 tenant to block these extensions. But, because the SLK-based attack is just the next attack in a long line of those to come, it’s as important to teach users to be on their toes related to inbound emails, looking for red flags that might be malicious.
Share
JUL










About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com