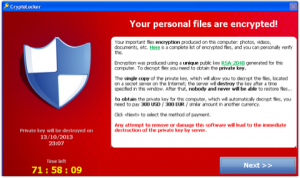
 This is hot off the press. Yesterday Malwarebytes announced a beta of a new anti-crypto software product designed to stop CryptoWall4, CryptoLocker, Tesla, and CTB-Locker. You can download the beta here.
This is hot off the press. Yesterday Malwarebytes announced a beta of a new anti-crypto software product designed to stop CryptoWall4, CryptoLocker, Tesla, and CTB-Locker. You can download the beta here.
According to Malwarebytes:
Continue Reading →“Malwarebytes Anti-Ransomware monitors all activity in the computer and identifies actions which are typical of ransomware activity. It keeps track of all activity and, once it has enough ...
JAN

 A virtual private network, or VPN, is a type of network computer connection that creates a private encrypted communications channel, commonly called a “tunnel,” when using insecure networks, such as in hotels and coffee shops, or when communicating over the Internet. Many businesses provide a VPN connection for their mobile and traveling employees. This means that when out of the office, a worker can open the VPN and be connected to ...
A virtual private network, or VPN, is a type of network computer connection that creates a private encrypted communications channel, commonly called a “tunnel,” when using insecure networks, such as in hotels and coffee shops, or when communicating over the Internet. Many businesses provide a VPN connection for their mobile and traveling employees. This means that when out of the office, a worker can open the VPN and be connected to ... There are many online accounts that would be bad to lose control of, such as your Amazon, eBay, PayPal, or bank account. But by the far the worst account to lose is your email account. If I can trick you into giving me your email user ID and password, by using a phishing email, or phone pretext call, I will be in. I can start off by simply observing, as I read your ...
There are many online accounts that would be bad to lose control of, such as your Amazon, eBay, PayPal, or bank account. But by the far the worst account to lose is your email account. If I can trick you into giving me your email user ID and password, by using a phishing email, or phone pretext call, I will be in. I can start off by simply observing, as I read your ... This post is a shout out to my peers in the cybersecurity profession, and especially those who would like to join us. I found these sites in two separate posts on
This post is a shout out to my peers in the cybersecurity profession, and especially those who would like to join us. I found these sites in two separate posts on  Quick answer: Yes it can! A
Quick answer: Yes it can! A  Passwords – Is mine strong enough? How do I know? Every time I write a password article I feel as if this subject has already been done to death by me and others. But I always get more positive feedback on this subject than others I consider more interesting, so we offer the following suggestions:
Passwords – Is mine strong enough? How do I know? Every time I write a password article I feel as if this subject has already been done to death by me and others. But I always get more positive feedback on this subject than others I consider more interesting, so we offer the following suggestions:
 I am getting posts from the FBI and the
I am getting posts from the FBI and the