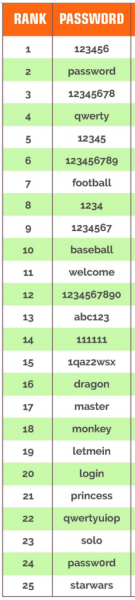
 Here are the 25 most commonly used passwords for 2014. If your password is on this list, please understand that these passwords are among the first tried when automated password cracking software is used by a cyber-criminal. So if yours is here, change it now.
Here are the 25 most commonly used passwords for 2014. If your password is on this list, please understand that these passwords are among the first tried when automated password cracking software is used by a cyber-criminal. So if yours is here, change it now.
Passwords are becoming problematic for several reasons. The first, IMHO, is the use of email addresses as the user ID portion of the User/Password duo. The reason for this is that an email address is a unique identity item. I do remember, back in the day, trying to create a unique user name could be a long and frustrating process. Still, it is just too easy to get someone’s email address, and there you are, halfway home. I would prefer to use something that I create as my user name, and I appreciate it when I have that option.
The second reason passwords are not secure is that solving for a password is so easy. Passwords are stored in an encrypted form, but enterprising cyber-criminals have created tables of encrypted possibilities and plain-text solutions, so if I have a new list of password hashes, I can simply compare my encrypted passwords to the table using automated software, and solve for passwords in a few minutes. Even password length matters little if I am just comparing two lists of characters using automation.
So then we move to two factor authentication. Now I need my user name, my password, and in my own case, a 6 digit PIN that is replaced every 30 seconds by Google Authenicator, and displayed on my phone in the Authenticator app. This means that someone who has cracked my password also has to have my phone to log in to many of my accounts. With two-factor authentication I am considerably more secure.
Is there more that can be done? Tomorrow, we will look at another technology making its way into the world of authentication called “adaptive authentication.”
More Information
ShareFEB




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com