 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
Google AI teaches itself ‘superhuman’ chess skills in four hours
Google’s “superhuman” AlphaZero artificial intelligence (AI) taught itself chess from scratch in four hours. Then, it wiped the floor with the former world-leading chess software, Stockfish 8. Out of 100 matches, AlphaZero won 28 games and drew (tied) the remaining 72.
So long AOL Instant Messenger
As AIM rides off into the sunset, let’s reflect on its role in preparing people for today’s digital messaging methods.
Hidden keylogger found on HP laptops ITProPortal
- Leftover Synaptics debugger puts a keylogger on HP laptops The Register
- HP issues update to remove ‘accidental’ keylogger from laptop driver The INQUIRER
- HPSBHF03564 rev 1 – Synaptics Touchpad Driver Potential, Local Loss of Confidentiality | HP® Customer Support HP Support
- HP laptops found to have hidden keylogger BBC News
TA14-017A: UDP-Based Amplification Attacks
Original release date: January 17, 2014 Updated on: December 4, 2017
Systems Affected
Certain application-layer protocols that rely on the User Datagram Protocol (UDP) have been identified as potential attack vectors. These include
- Domain Name System (DNS),
- Network Time Protocol (NTP),
- Connection-less Lightweight Directory Access Protocol (CLDAP),
- Character Generator Protocol (CharGEN),
- Simple Service Discovery Protocol (SSDP),
- BitTorrent,
- Simple Network Management Protocol version 2 (SNMPv2),
- Kad,
- Portmap/Remote Procedure Call (RPC),
- Quote of the Day (QOTD),
- Multicast Domain Name System (mDNS),
- Network Basic Input/Output System (NetBIOS),
- Quake Network Protocol,
- Steam Protocol,
- Routing Information Protocol version 1 (RIPv1), and
- Lightweight Directory Access Protocol (LDAP).
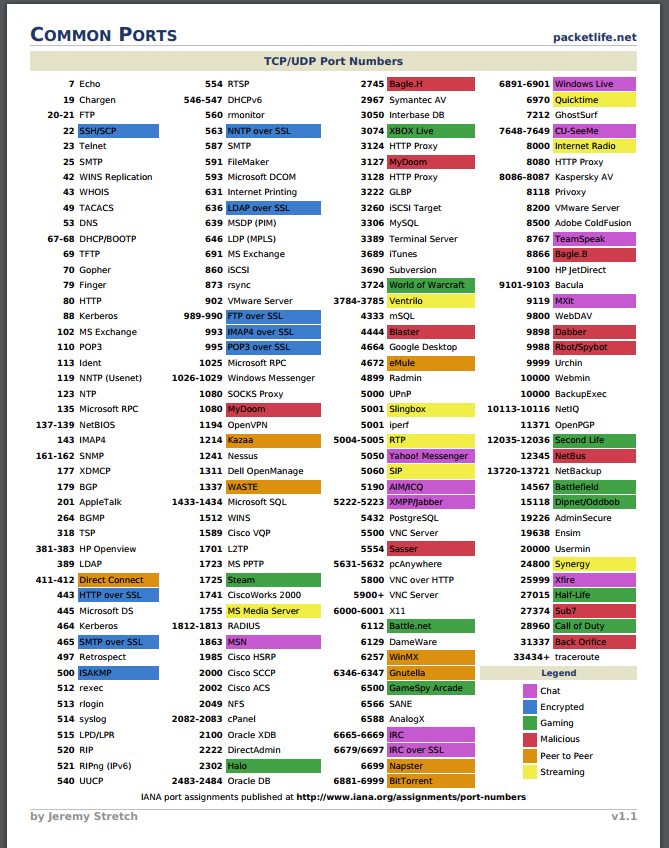
Common Ports
Share
16
DEC
DEC




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com