 We continue to hear from security researchers and professionals that an astonishing 95% of all exploits begin with someone opening an attachment or clicking a link on a phishing email. I have a client where two different employees opened the attachment on an email from “FedEx” and became infected with crypto-malware. These incidents happened nearly a week apart, and you think that the second guy might have learned something from the first guy’s experience.
We continue to hear from security researchers and professionals that an astonishing 95% of all exploits begin with someone opening an attachment or clicking a link on a phishing email. I have a client where two different employees opened the attachment on an email from “FedEx” and became infected with crypto-malware. These incidents happened nearly a week apart, and you think that the second guy might have learned something from the first guy’s experience.
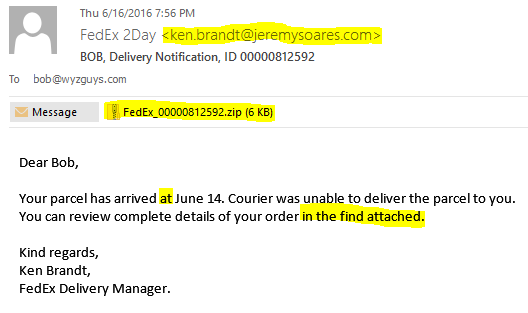
Be alert to emails that come from a well-known company, but the email address doesn’t match up. FedEx 2 Day emails should not be from someone at jeremysoares.com, but from fedex.com. The zip file attachment in this email contained a remote access Trojan called JS/TrojanDownloader.Nemucod.AEI, according to Virus Total. It probably would have launched a crypto-malware attack, had I installed the Trojan.
I also highlighted some fractured grammar in the body of the message. Most phishers are pretty good with their English syntax these days, but when you get something like this that reads like Google Translate it is a distinct red flag.
I make a habit of forwarding emails like this one to scan@virustotal.com. You can too. All you need to do is change the subject line to “SCAN” (without the quotes). In a few minutes you will get a report back with the bad news.
A word of warning – sometimes I get an email showing the the email was clean, but I rarely open the suspicious ones anyway. A link or HTML page may be malware free, but still transport you to a website that is a malware distribution site.
Never ever open an attachment or click on a link in an email without confirming that the email is legitimate. You can check both links and attachments at VirusTotal. When in doubt, call the sender to confirm the email was really from them.
The United States Computer Emergency Readiness Team (US-CERT) published an article on their site that discusses the issue in depth, and offers good advise on how to recognize and avoid falling for a phishing scam. A worthwhile read, so take a minute an click through.
ShareJUL




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com