This is the second of a three-part series of articles about TOR. On Monday we took a look at the surprising origins of the TOR network. Today we will be taking a look at how TOR works.
HOW TOR WORKS
To use TOR, a person just needs to go to The TOR Project , and download an install the TOR web browser. Then it makes sense to read the TOR warning document. The rules include:
- Use the TOR browser
- Don’t torrent over TOR
- Don’t enable or install browser plugins
- Use HTTPS versions of websites
- Don’t open documents downloaded through TOR while online
- Use TOR bridge relays
- Promote TOR usage
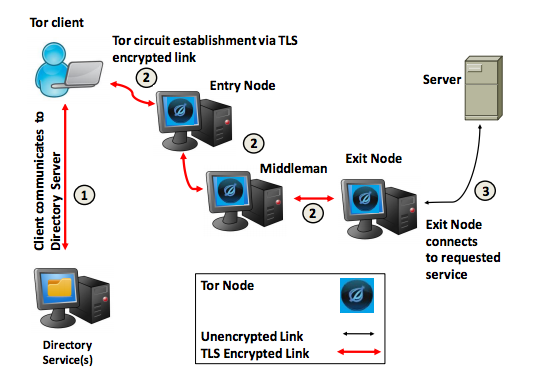
Your online session will be routed through the TOR network of over 6000 relays. Your TOR browser establishes a TLS encrypted link to a TOR entry node. Then data packets including the originating IP address are encrypted multiple times (multi-layered encryption, like an Onion – get it?) then the traffic is sent through a number of TOR relay nodes. Each relay node removes one layer of encryption, and forwards the data packets to the next relay in the virtual circuit. TOR also allows packet streams to be multiplexed, so that packets in a single session may be routed over different sets of relays, further anonymizing the session. The data packets final reach a TOR exit node, where the last layer of encryption is removed, and the data is sent to its destination.
Herein lies one of the exploitable weaknesses of TOR. Traffic leaving the exit node is UNENCRYPTED. The originating IP address is still concealed, but the contents of the session are available in plain text. If an exit node is compromised, or perhaps created by a government agency and added to the TOR network, all TOR traffic leaving this exit node is susceptible to surveillance. In fact, in July 2014, the TOR project detected just such a group of relays and removed them from the TOR network. This would have coincided with the time frame of the FBI’s “Operation Onymous” (not anONYMOUS any longer) which took down Silk Road.
But we are ahead of ourself. For the most part, communications over the TOR network is still the most secure way to communicate over the Internet, beating out other anonymizer services and VPNs (virtual private networks). On Friday we will take a look at some of the recently uncovered weaknesses of the TOR network.
Sources for more information:
- Wikipedia – Tor (anonymity network)
- TOR Project
- TOR Warning Document
- NSA “Tor Stinks” Presentation
- eWeek – Tor Puts NSA at Odds With Browser’s U.S. Navy Creators, Other Agencies
- Vice.com – How the NSA (Or Anyone Else) Can Crack Tor’s Anonymity
- Forbes – How Did the FBI Break TOR?
- Sophos – Can You Trust TOR’s Exit Nodes?
- Business Insider – Both Of The Men Accused Of Running The Silk Road Made The Exact Same Mistake
JUL




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com