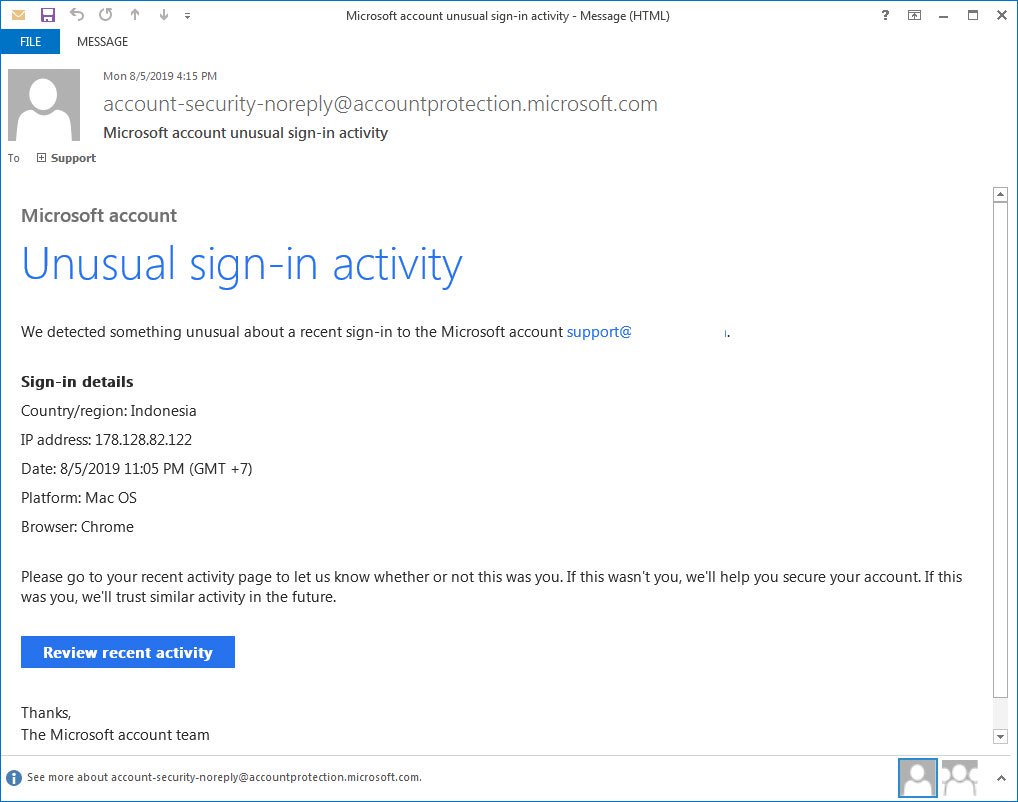
The title may see a little harsh, but a recent survey according to Keeper Security’s 2019 SMB Cyberthreat Study is that 66% of SMB business leaders do not believe they will be victimized by at cyber-attack. That’s two out of three business owners. I would love to say I’m shocked, but my experience with my own clientele would confirm it.
The title may see a little harsh, but a recent survey according to Keeper Security’s 2019 SMB Cyberthreat Study is that 66% of SMB business leaders do not believe they will be victimized by at cyber-attack. That’s two out of three business owners. I would love to say I’m shocked, but my experience with my own clientele would confirm it.
According to the Poneman ...
Continue Reading →AUG