 We have talked about new Office document exploits that don’t require macros to run. Here is a new one with more twists and turns than a mountain road. Trustwave has reported instances of a new attack that starts as a spam or phishing email with a Word document (.DOCX) attachment. Open the Word document and it will call out for another document download, this one in Rich Text Format (RTF) that takes advantage of known vulnerability CVE-2017-11882. This document downloads an HTML document (HTA), that spawns Powershell with a Visual Basic script (VBS), which finally downloads a keylogger in PHP. If all this has your head spinning, it is having a similar effect on the anti-malware software we rely on to protect us from these sorts of attacks. Here’s the path again in a simple flowchart.
We have talked about new Office document exploits that don’t require macros to run. Here is a new one with more twists and turns than a mountain road. Trustwave has reported instances of a new attack that starts as a spam or phishing email with a Word document (.DOCX) attachment. Open the Word document and it will call out for another document download, this one in Rich Text Format (RTF) that takes advantage of known vulnerability CVE-2017-11882. This document downloads an HTML document (HTA), that spawns Powershell with a Visual Basic script (VBS), which finally downloads a keylogger in PHP. If all this has your head spinning, it is having a similar effect on the anti-malware software we rely on to protect us from these sorts of attacks. Here’s the path again in a simple flowchart.
EML >> DOCX >> RTF >> HTA >> PS >> VBS >> PHP
Typical email subject lines include:
- TNT STATEMENT OF ACCOUNT – {random numbers}……………
- Request for Quotation (RFQ) – <{random numbers}>
- Telex Transfer Notification
- SWIFT COPY FOR BALANCE PAYMENT
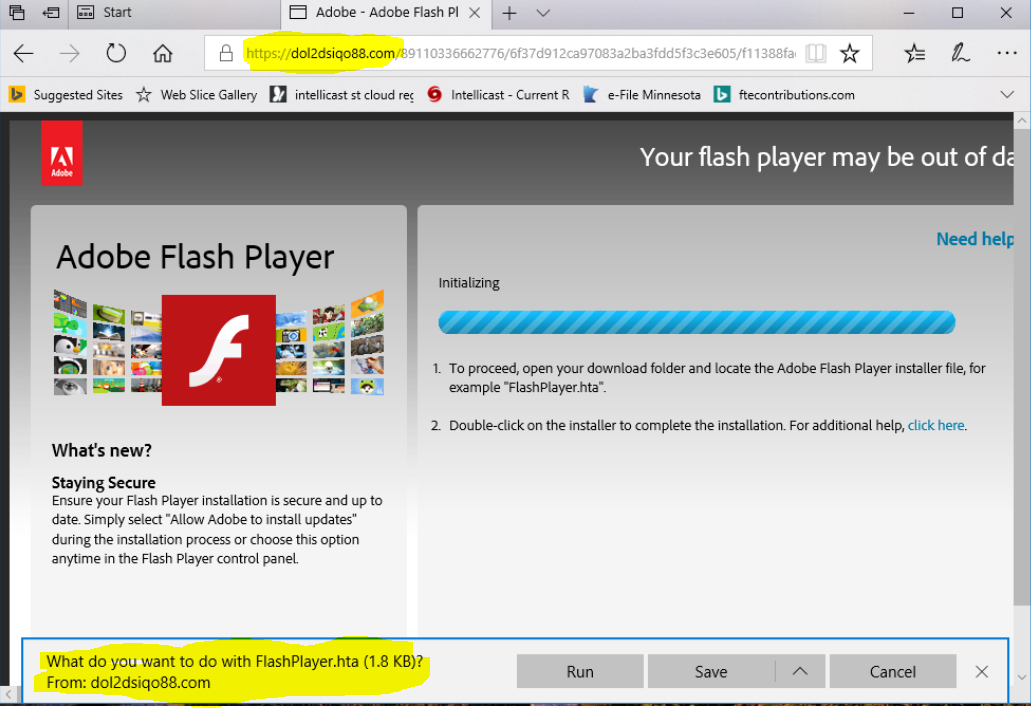
I removed a bit of malware from a client system recently, and it had spawned a browser page that looked a lot like and Adobe Flash Player update. See the following image. Notice the attempted download of the HTA file, and the obviously wrong web address in the browser address bar.
You will need to be on the lookout for pages like this one. Running the HTA file would have installed the keylogger. A keylogger is a malware program that captures your keystrokes as you type, and is used for collecting user names, passwords, credit card number, social security numbers, and other personal information.
I encourage you to check out the Trustwave article for more examples and images.
More information:
-
Multi-Stage Email Word Attack Without Macros – Trustwave
MAY




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com