 A new exploit is using Microsoft Office documents to deliver malware. This is different from the reanimated macro exploits. If this exploit, the target will receive an Office document, such as a Word file, as an email attachment. Opening the attachment causes a malicious HTML application to be downloaded from the attackers C2 server. This is executed as an .hta file, disguised as an RTF file. The result is the attacker has complete access to the targeted computer. Once the malware installation is complete, the victim is show a fake Word document.
A new exploit is using Microsoft Office documents to deliver malware. This is different from the reanimated macro exploits. If this exploit, the target will receive an Office document, such as a Word file, as an email attachment. Opening the attachment causes a malicious HTML application to be downloaded from the attackers C2 server. This is executed as an .hta file, disguised as an RTF file. The result is the attacker has complete access to the targeted computer. Once the malware installation is complete, the victim is show a fake Word document.
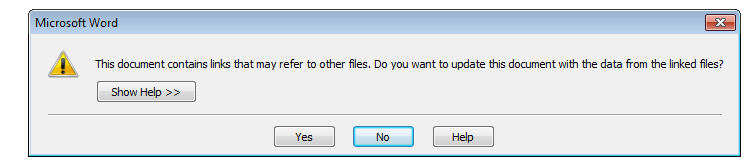
All versions of Office including Office 2016 are vulnerable to this exploit. The exploit takes advantage of Windows Object Lining and Embedding (OLE) functionality. Opening the attachment often spawns this dialog box.
Microsoft sent out an update on April 11th to address this security vulnerability, so if you are keeping up on Windows updates, you should be fine. But there are other actions you can take to protect yourself from this exploit, and the variations that are bound to appear later.
- Do not open attachments unless you have confirmed them with the sender.
- Better yet, forward the email with the attachment to scan@virustotal.com. Change the subject line to SCAN, and wait for a response from VirusTotal. The attachment will be scans, and if the attachment contains malware, you will be notified in the scanner results email. This process takes less than 10 minutes.
- This particular exploit cannot bypass Office Protected View. This feature should be enabled if it is not already. to check if this feature is enabled:
- Click the File tab in the upper left corner.
- Select Options.
- Select Trust Center in the left pane.
- Click Trust Center Settings.
- Select Protected View.
- Make sure all three options under Protected View are checked.
- If not check them and click OK.
These tips should protect you from this new Office exploit.
More information:
ShareAPR




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com