 There is a new email attachment exploit making the rounds, that uses a file type called a disk image. The file extension for this kind of file is ISO. ISO files are not inherently dangerous, and in the exploit work much the same way that a ZIP attachment works. This file type can sneak past email security filters because it is generally seen as benign, while containing anything that the creator wants to include.
There is a new email attachment exploit making the rounds, that uses a file type called a disk image. The file extension for this kind of file is ISO. ISO files are not inherently dangerous, and in the exploit work much the same way that a ZIP attachment works. This file type can sneak past email security filters because it is generally seen as benign, while containing anything that the creator wants to include.
If you have ever installed Linux on a computer, then you are familiar with the ISO packages that can be downloaded to install the Linux operating system. But ISO files do not have to contain an operating system. You could create an ISO of a CD or DVD in order to create a copy of a music album or a movie. Clever cyber-criminals are putting executable malware files in these ISO attachments.
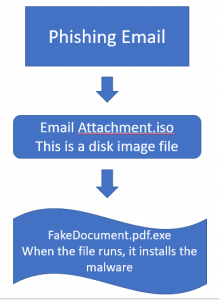
The way this works is diagrammed above. A phishing email with an ISO attachment shows up in your inbox. Maybe you are not familiar with the ISO file type, or maybe you are, but in either event, if you decide to open the file, the Windows operating system will treat the ISO as if it were an optical drive or USB drive, and mount it to the operating system. Windows will even give it a drive letter, and an icon in the Windows Explorer applet. Then windows will “play” the content. If the content is an executable file, your computer will install the malware program.
Many of these attacks also use a double file extension, something like fakedocument.pdf.exe. The terminal EXE indicates the file is executable. Because Windows no longer displays common file extensions, you may only see fakedocument.pdf. Looks like a PDF file, should be safe, right? In this case, not so much.
Lately this exploit has been coupled with a BitCoin related hook, with the ISO file going out as attachment to an email advising you of a large deposit of BitCoin in your BitCoin wallet. You are asked to open the ISO file for details about the transaction and instruction on how to collect your crypto-currency.
Ways to protect yourself from this type of attack include:
- Watch for spelling and grammar mistakes. These guys are seldom native English speakers, so wacky syntax can be a clue.
- ISOs aren’t a common file attachment type. This should just be added to your list of attachment file extensions to avoid.
- Reveal your file extensions. Microsoft decided we don’t need to see file extensions any more, because people didn’t understand what they are for. I disagree. Open Windows Explorer, click on the View tab, and turn on File name extensions.
- Don’t trust links or attachments. Find your own way to the web site, through typing the address or using a saved favorite or bookmark.
Additionally, if you never set up a BitCoin wallet, then you DON’T HAVE a BitCoin wallet. And strangers are not going to send you a pile of money, regardless of the currency type. Don’t be tricked just because it is new, exotic and kind of exciting. “Ooh! Someone sent me BitCOin!” Probably a Nigerian Prince, no doubt.
More information:
ShareFEB




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com