One of these URLs will open your Gmail account. The other will take you to a replica phishing landing page to steal your Gmail password. Can you tell which is which?
![]()
If you chose the first one as fake, and the second one as genuine, you are correct. If not, you are “pwned” or owned by a cyber-criminal. Want to check and see if your email account has been pwned? There is a trustworthy site, https://haveibeenpwned.com/, run by well known security researcher Troy Hunt. You can check if any of your email accounts have been breached. Enter your email address and hit the button.
This sort of trickery is being used to hijack Gmail accounts, as reported on January 12th on the WordFence blog. We shared the WordFence article out on LinkedIn and Facebook already, but if you haven’t read it, I encourage you to do so. Especially if you have a Gmail account.
If the URL or web address in the address bar of your browser doesn’t start with an http: or https:, then it is definitely an address that will lead you into trouble. If you don’t know what I mean by “address bar,” look to the top of this page, for the white box under the tab that says “http://wyzguyscybersecurity.com.” That box is the address bar, and it will show you the address of the web page you are looking at right now.
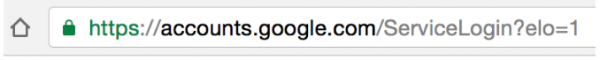
One of the ways to tell if an email is a phishing exploit is to examine the URLs or web age addresses that are used by the links in the message. But if you don’t know what a web address is supposed to look like, how can you avoid a bad link?

Let’s look at the address above. A web site address should always start with http:// or https://. Many modern web browsers, such as Google Chrome, don’t always display this part. This is the “protocol” or the communication method. HTTP stands for hypertext transport protocol, and HTTPS is the secure encrypted version of the protocol. There are other protocols that you may see from time to time, such as FTP, SFTP, but a proper web address will always start with HTTP.
Beyond the double slash we have the main part of the address – “accounts.google.com.” There are three parts separated by periods. From right to left (backwards) they are the top level domain (.com), the domain (google), and the sub-domain (accounts.)
Let’s start at the far right end with the TLD .com. Internet addressing is hierarchical, with the highest part on the right end. In addition to .com. there are other TLDs such as .net, .gov, .org, and so forth. And there are country TLDs as well, .us for the Untied States, .ca for Canada, .ru for Russia, .cn for China, and .in for India. Wikipedia has a great list in this article. Sometimes phishing links end in .ru, .cn. or .in. This would be a good clue that your email is a phishing exploit.
The next part, “google” is the domain name. Domain names are in essence leased from a Domain Registrar, and identify a property like a web site on the Internet. A domain name is controlled in some ways by the organization that is running the top level domain. So in order to find “google.com” your browser asks it’s ISP’s Domain Name Server where to find google.com, and that server asks the .com TLD DNS server for directions. This is over simplified, but in essence this is how it works.
Many scammers will register close misspellings of a domain name, such as goggle.com or gooogle.com in order to trick their target into becoming a victim. This is another thing to be looking for in the address bar of your browser.
The last part, “accounts” is a sub-domain. Whoever controls the domain may create any sub-domains they wish. Sub-domains are used to segment and organize the name space and web resources of the domain itself. A sub-domain may have its own sub-domain, so “email.accounts.google.com” would be an allowable address.
Email phishing exploits take advance of this by registering a domain name, and using sub-domains to make the URL appear legitimate. So if I register “ice365.com” I can add “off” as a subdomain and get http://off.ice365.com. This looks very close to Microsoft’s domain for it’s Office 365 product line, and could be used in a phishing exploit to harvest the credentials of Office365 users. Or something like http://paypal.accountsettings.com. The domain “accountsettings.com” is registered by the scammer, and they create the sub-domain “paypal” to use in an exploit targeting PayPal users.
![]()
The URL above is even trickier. In this exploit, you would receive an email, maybe from someone you know who has already been hijacked. There is an attachment, and opening the attachment loads some code embedded in the attachment. This code creates a realistic looking Google login page right on your computer, and if you enter your user name and password, it is sent to the attacker, and your account will be hijacked in a moment.
The URL starts with “data:text/html.” This is clearly not normal, but the next part is, and for many people that is enough to trick them into giving away their user credentials.
What can you do to protect yourself from these sorts of credential stealing exploits? Two-factor authentication is your best defense, because without your 6-digit 2FA passcode, the user Id and password they just stole will not be enough to take over the account.
If you own or manage a business or other organization, hire an instructor to come in and do some cybersecurity awareness training with an emphasis on phishing detection and avoidance. You can also hire someone to run a phishing simulation on a periodic or on-going basis. When it comes to social engineering exploits such as phishing, education and awareness are the best defenses. Most of us were raised to be trusting and helpful. We need help to be come vigilant and suspicious.
More information:
ShareJAN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com