Now that you understand why your website may have been hijacked, you want to know if your website has been hijacked. Finding out your website has been hijacked is not necessarily easy. Sometimes site owners think they have been attacked, when it was something innocuous. But discovery of a hijack can happen a number of different ways, and many of them can be embarrassing.
- Your web hosting provider informs you of a malicious infection or activity and takes your site offline.
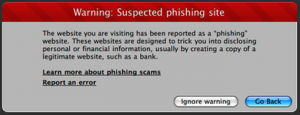
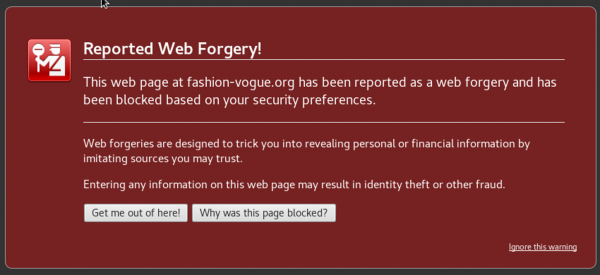
- Your web browser, or those used by your customers, spawns a warning.
- Your computer’s malware scanner, or those used by your customers, alerts on your site
- Your customer gets infected on your site and contacts you.
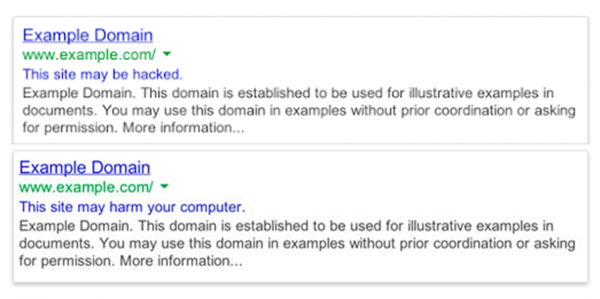
- Your site may show up in Google search results as dangerous or compromised
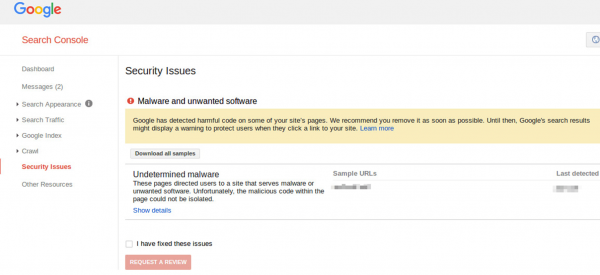
- Your Google Search Console account warns you about a malware infection.
Examples of these warnings follow. These are common indications that your site has been compromised.
Share
18
APR
APR




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com