 We’ve all seen this on National Geographic. A lion, tiger, or other top predator hides near a water hole and waits for some sort of four-legged lunch to stop by for a drink. Cyber-criminals and other attackers are using a similar technique to download and install malware from niche or industry specific websites to computer systems at targeted businesses. Here’s how it works.
We’ve all seen this on National Geographic. A lion, tiger, or other top predator hides near a water hole and waits for some sort of four-legged lunch to stop by for a drink. Cyber-criminals and other attackers are using a similar technique to download and install malware from niche or industry specific websites to computer systems at targeted businesses. Here’s how it works.
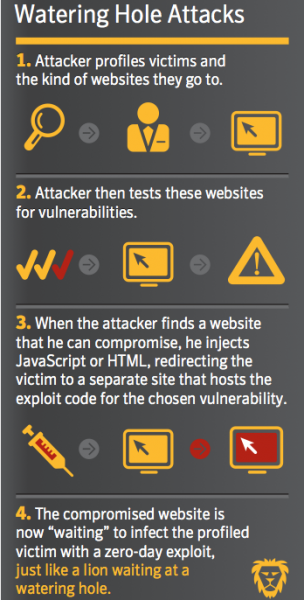
- The attacker will start by researching the intended target business to discover what websites they use frequently, among other information such as names, titles, job functions and email addresses of employees. This is the reconnaissance phase.
- The websites in question are typically industry-specific low traffic websites that exist to support businesses in that industry. For instance, it may be the website of a supplier or wholesaler, professional association, or some other supporting organization. These small market websites tend to be poorly secured, and may be easily hijacked by taking advantage of security misconfigurations, or broken authentication and session management, or by using standard exploits such as SQL injection. Credentials for these sites may be harvested through spear-phishing or social engineering attacks, or purchased on the Dark Web.
- Once the attacker has taken control of the website, they will add malicious downloadable code to the home page or other high traffic pages on the website. Or they may inject malicious JavaScript or HTML code to redirect the victim to another site where the malware is hosted. Unsuspecting site visitors are infected with the malware, generally something like a remote access Trojan horse, keylogger, or a combination product such as a banking Trojan or encryption ransomware program.
- The final phase is to use the foothold gained at the targeted company to complete the mission and obtain the final objective. This may be a financial or wire transfer exploit, a ransomware attack, or the exfiltration of sensitive or proprietary information and documents.
Watering hole attacks are not as common as phishing or spear-phishing attacks, but are on the rise. They are difficult to detect and typically target hard to hack higher-security organizations by breaching their low-security employees, business partners, network-connected vendors or an unsecured wireless network. This makes them a difficult threat to secure against, detect or mitigate.
Defending against this exploit is best accomplished by:
- Continually updating your web browsers to the most current and most secure versions. The newer browsers may be able to warn you that a site is infected, or detect and prevent the malicious download from happening. Currently, the best browser in this class in Microsoft’s new Edge browser. But the latest versions of Chrome, Firefox, and Safari all have important security safeguards that can protect you from this exploit.
- Applying operating system and software updates in a timely manner. Like we’ve said a hundred times!
- Use network traffic analysis to detect connections to external command and control servers used by the attackers.
- Keep an eye on threat exchange websites for information about new exploits and advanced persistent threat activities that may be targeting your industry. AlienVault’s Open Threat Exchange is a good example.
Check out the articles below for a deeper look at this issue. And remember just because you have safely used a website many times in the past, today it could be hosting something bad for your business. Keep your guard up and stay safe.
More information:
- WyzGuys – Microsoft Edge Browser
- What is a Watering Hole Attack
- Spear phishing still popular, but more watering hole attacks coming
- Defending against watering hole attacks: Consider using a secure VM
- Web Injection Process Used in Watering Hole Attacks
- Chinese hackers are by-passing web privacy tools, say researchers
- Threat Encyclopedia: Watering Hole 101
JAN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com