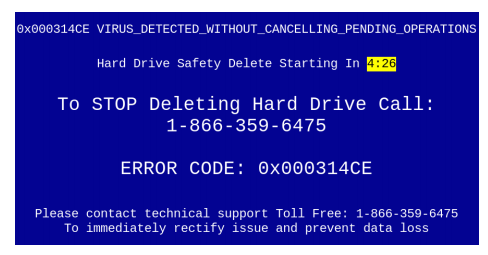
 We have reported a few times about the tech support scammers who use cold-calling phone lists or browser pop-ups with 800 number “support” lines to trick people into paying $300 or more for “malware removal” and other services that the computer doesn’t need. And the pop-ups can be scary and convincing as in the example image.
We have reported a few times about the tech support scammers who use cold-calling phone lists or browser pop-ups with 800 number “support” lines to trick people into paying $300 or more for “malware removal” and other services that the computer doesn’t need. And the pop-ups can be scary and convincing as in the example image.
Naked Security recently reported on the work of researchers from Stony Brook University on how the tech support scam works from the scammers side, where these teams are located, what sort of software tools they use, how they monetize their activities, and how much money they make.
Using tactics such as “typo-squatting” or registering thousands of close misspelling of popular domain names (i.e. Twittter.com or Gooogle.com). Hosting their replica web pages on content delivery networks or hijacked websites and servers. Using system events such as stopped services or drivers to confuse the victim into believing their system is infected or compromised. Using legitimate remote access tools such as LogMeIn Rescue and Teamviewer to take control of the victim’s PCs, and then charging ridiculous amounts to install unnecessary software to clean the system. They are raking in millions of dollars.
As we have said before, if this happens to you do not call the provided tech support number. Call your regular tech support provider. If they called you, please just hang up the phone. Never give them (or anyone else who is calling you for that matter) your credit card number, or worse yet, bank routing and account numbers.
More information:
ShareMAY




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com