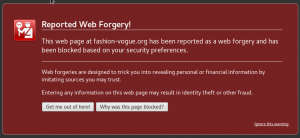
If you were hit with credit card fraud this year, you are not alone. 15% of Americans surveyed by CompareCards, a LendingTree subsidiary, reported they had been victimized in 2017. Fraud can happen without losing your card. While card companies and banks are more alert to fraud than ever, cardholders are often the first to discover the fraudulent use of their card.
If you were hit with credit card fraud this year, you are not alone. 15% of Americans surveyed by CompareCards, a LendingTree subsidiary, reported they had been victimized in 2017. Fraud can happen without losing your card. While card companies and banks are more alert to fraud than ever, cardholders are often the first to discover the fraudulent use of their card.
The two main types of card fraud ...
Continue Reading →MAY