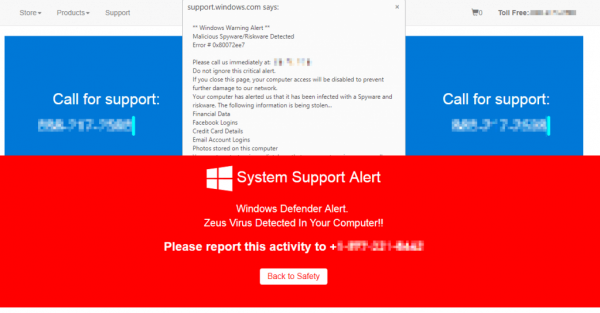
Bad actors are using compromised WordPress.com accounts and the popular Jetpack plugin to add a malicious plug-in of their own that turns compromised websites into a vehicle for perpetrating a fake tech support scam. Attackers are using stolen user names and passwords from other breaches and trying these credentials on WordPress.com to find accounts. They are even searching whois records for website domain names registered with the same email account as the stolen user name.
Continue Reading →JUL