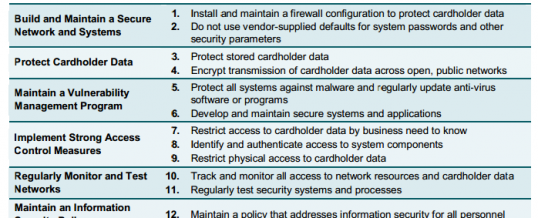
If you accept credit cards for payment in your business, then you are subject to the Payment Card Industry Data Security Standard or PCI-DSS. Up to now, this standard has really been more about compliance, but this year the Payment Card Industry is definitely focusing on real 24/7 365 security. The industry has been hit hard in the last two years by the BackOff POS exploits that have affected major retailers such as Target, Home Depot, and Staples, as well ...
Continue Reading →JAN