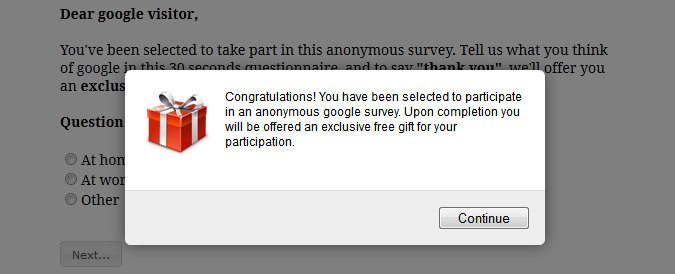
Phishing is still the number one tactic used by malicious actors to collect passwords and other information. Phishing works because the attacker is able to create an email that is believable and looks realistic. The best ones appear to come from a customer, supplier, coworker or other trusted source, and the content makes sense for your business or personal life. The most successful way to prevent phishing from ruining your day ...
Phishing is still the number one tactic used by malicious actors to collect passwords and other information. Phishing works because the attacker is able to create an email that is believable and looks realistic. The best ones appear to come from a customer, supplier, coworker or other trusted source, and the content makes sense for your business or personal life. The most successful way to prevent phishing from ruining your day ...
FEB