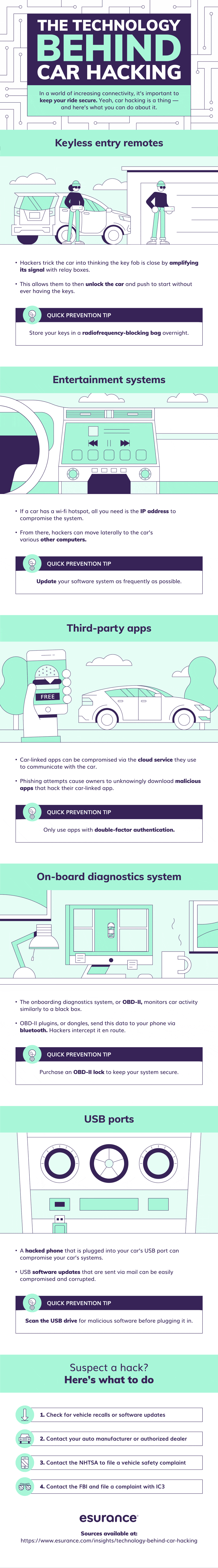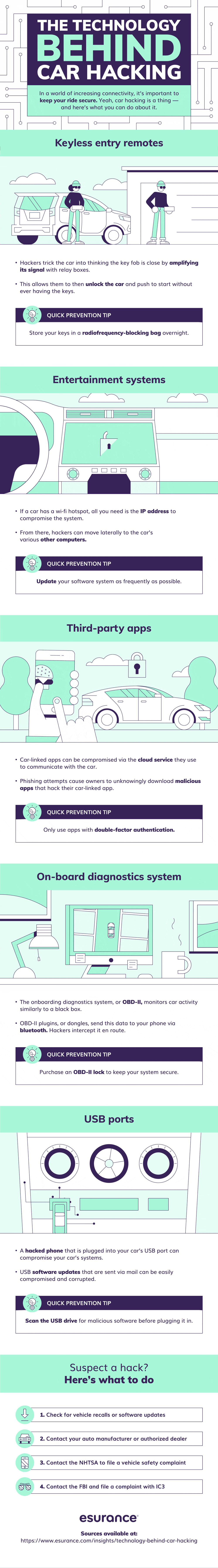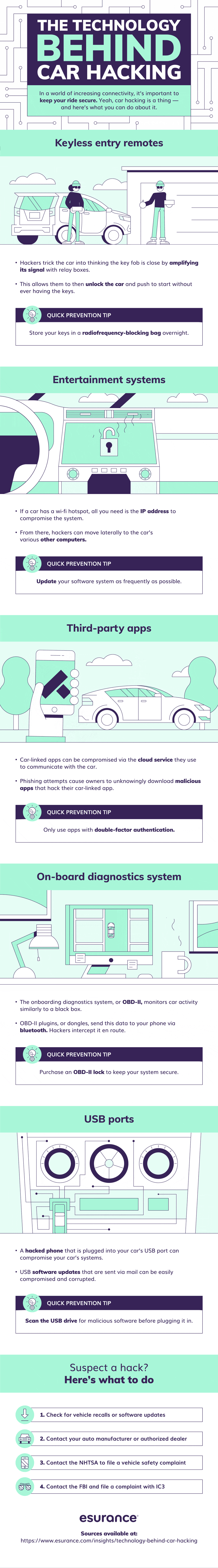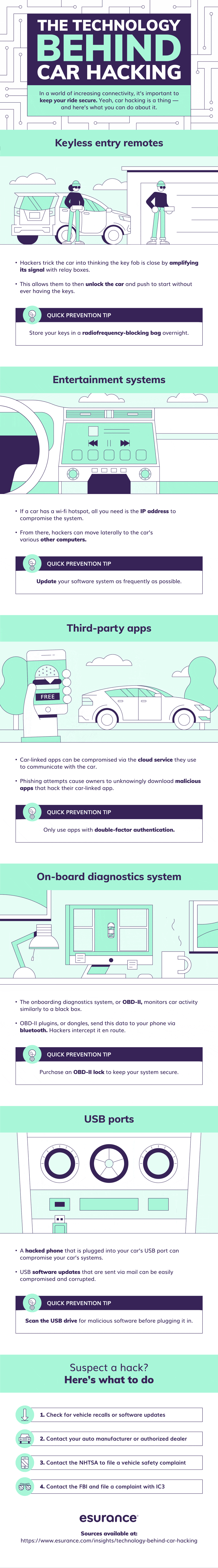
Identity theft is probably one of the most serious crimes that can happen to you. The bad news – identity theft in one fashion or another is likely to happen to all of us. In any given year, one in fifteen people will suffer identity theft. There are many ways that your personal information way end up in the hands of ...
Identity theft is probably one of the most serious crimes that can happen to you. The bad news – identity theft in one fashion or another is likely to happen to all of us. In any given year, one in fifteen people will suffer identity theft. There are many ways that your personal information way end up in the hands of ...
JUL