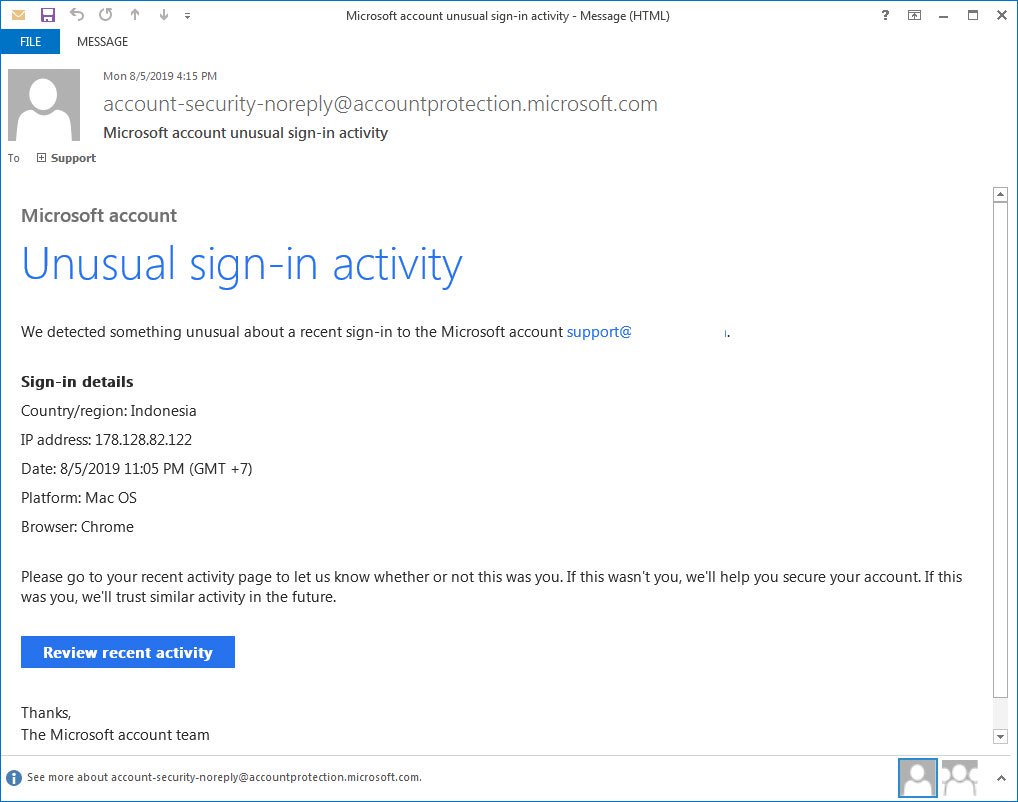
There is a very realistic spoofed phishing email making the rounds that looks so close the the real Microsoft alert email, as to be almost undetectable. They even spoof the legitimate sender address of “account-security-noreply@accountprotection.microsoft.com”. So even if you are looking for signs of chicanery, it will be difficult for most users to tell it is fake. See an example below.
AUG