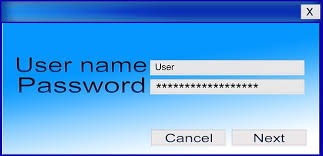
Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Why We Don’t Do Product Endorsements
Chef’s Special: Spoofing SharePoint Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, ...
Continue Reading →AUG




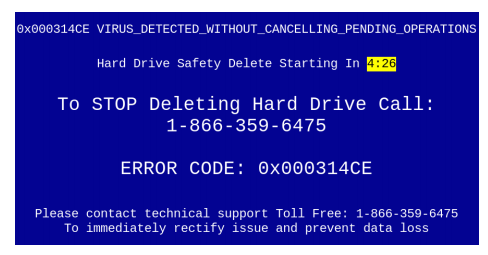
 It was recently reported in Naked Security that a Seattle television news crew interviewed an Office Depot employee who alerted them to the practice of selling in-store repair scams to customers who came in looking for computer help. This whistle-blower told a story where employees where encouraged and even pressured to run the chain’s “PC Health Check” on evey ...
It was recently reported in Naked Security that a Seattle television news crew interviewed an Office Depot employee who alerted them to the practice of selling in-store repair scams to customers who came in looking for computer help. This whistle-blower told a story where employees where encouraged and even pressured to run the chain’s “PC Health Check” on evey ... Today we are going to look at the symptoms that your computer may be displaying that are indications of a malware infection.
Today we are going to look at the symptoms that your computer may be displaying that are indications of a malware infection. A rare Tuesday post, but this is too important to wait. If you own a Lenovo computer, you need to uninstall the Lenovo Accelerator application. A recent
A rare Tuesday post, but this is too important to wait. If you own a Lenovo computer, you need to uninstall the Lenovo Accelerator application. A recent