During the last week and a half we have been investigating the sorry state of password security. Now for some more hopeful information. In this post, we will look at the current recommended standards for creating a secure password, and policy recommendations from the National Institute of Standards and Technology (NIST).
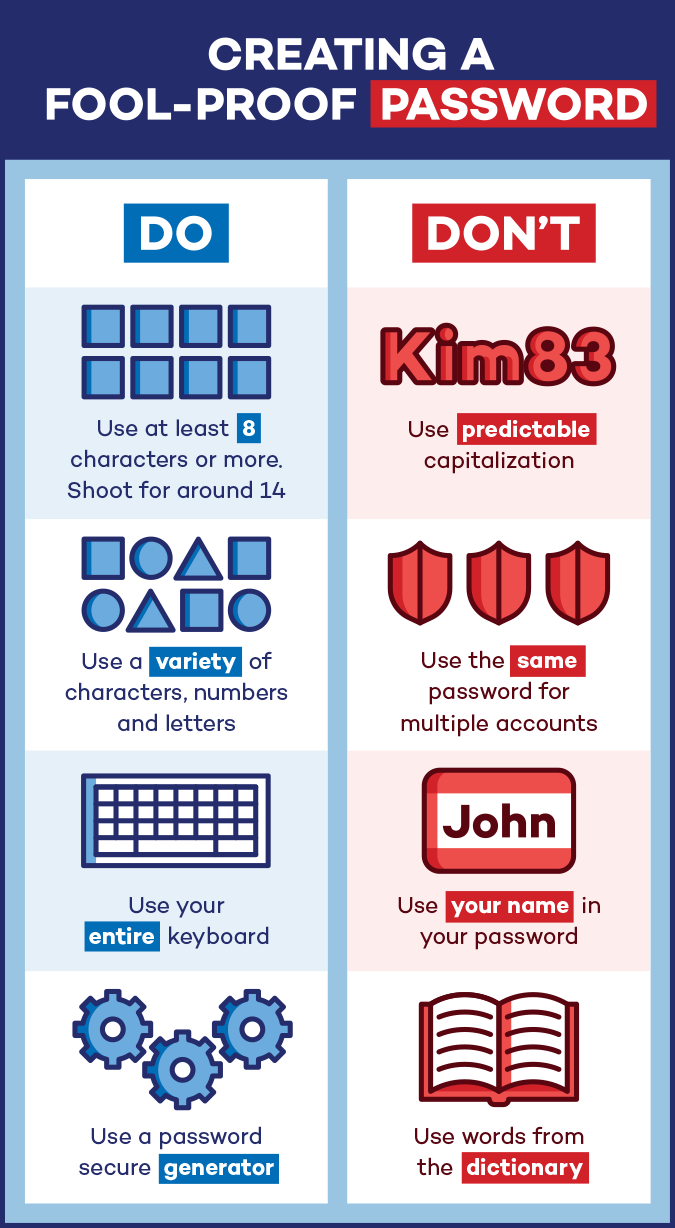
Our recommendations for password strength is to use passwords with at least 12 or more characters. The reason is that longer passwords are more secure in the face of automated password cracking. Typically, a 12-character password can take several years or even decades to solve using automated tools.
Nevertheless, password length is not effective against keyloggers, social engineering, or phishing exploits. If you give your password away to the attacker, length will not matter. The cure to this problem is two-factor or multi-factor authentication, known as 2FA, TFA, or MFA. This will create an additional layer of security for sites and applications where 2FA is enabled. In addition to your user name and password, something additional is required to complete the login. Frequently, it is a 6-digit, random, auto-rotating code for something such as a smart phone app.
There currently are 5 recognized factors that can be used for authentication:
- Something you know – Typically your password is the thing you know, but this can also be a PIN code, or the answer to a challenge question.
- Something you have – This could be a smartphone app such as Google Authenticator or Authy, for an RSA token. It might be a one-time code sent to your email or SMS, although these options are no longer considered fully secure. It might be a push notification sent to your smartphone that simply requires you to confirm your login attempt.
- Something you are – Also known as biometrics, this includes finger and palm print, iris and retina patterns, voice recognition, and facial recognition.
- Something you do – This is a new entry to the list and includes authentication technologies such as typing cadence and mouse movements. These methods focus on behaviors that are unique to the user.
- Somewhere you are – This is the second new method. This authentication method takes a look at your physical location on the planet, using GPS and/or IP address to confirm your identity. If you are logged in at your desk in Bloomington, Minnesota it would be impossible for you to log in during your session from someplace like Istanbul, Turkey.
Last year NIST, the National Institute for Standards and Technology, released Special Publication 800-63b. This document provides identification and authentication requirements for federal IT systems, but it’s recommendation are also followed by many state, county, and local governments, and large corporate enterprises as well. Some of the changes recommended by NIST were surprising in the way they killed off some of the sacred cows of authentication policy.
- Password length – NIST recommends longer passwords as the only useful defense against automated password cracking.
- Complexity requirements – NIST no longer requires using password complexity because it adds nothing to protect against automated brute-force password cracking. No more capital or lower case letters, numbers, and symbols.
- Enforced periodic password changes – NIST recognized that many studies have shown that forcing password changes at 30, 45, or 90 days results in people choosing easier passwords, and sometimes using a system, such as using the month, year, and a symbol (June2018!) NIST recommends password changes only upon suspicion or evidence of a breach.
- Biometrics – NIST says that the problem with biometrics is that they are not truly a secret, and they cannot be easily replaced. We leave finger and thumb prints all over the place, facial recognition can be defeated with a picture or 3-D printed face mask. Your optometrist has a record of your retina and iris patterns. Once breached, these features cannot be replaced. Biometrics are not to be used as the sole form of authentication.
- SMS and email codes – The problem with SMS is that the delivery channel is not secure and encrypted. This is also an issue with email, and if your email account has been hijacked, your attacker is getting the codes as quickly as they are delivered to you.
So your best bet for a stronger password is to make it longer and couple it with some form of two-factor authentication. I use Google Authenticator anywhere I can.
In our next and final post on this topic, we will look at password management solutions.
A special thanks to Panda Security for inspiring the content of this series and providing us with the infographics used in this series.
ShareJUN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com