Cyber-criminals are using a botnet to send phishing emails with the apparent purpose to test a new email attachment type. Over the course of three weeks starting August 10th, this cyber-gang released seven different types of phishing emails to over 3,000 banks around the world. They appear to be testing which of these several approaches is most successful at tricking recipients into opening the email attachment.
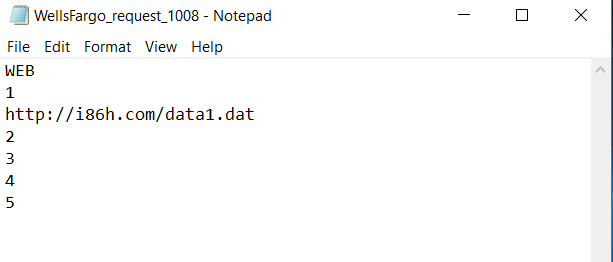
The attachment itself is also something different – Microsoft Excel Web Query files that use an .iqy extension. I was not familiar with this file type or what it does, but basically when the file is opened, it opens in Excel, and sends out a call to a web address to download additional “data.” In this case the data appears to be a remote access trojan (RAT) call FlawedAmmyy. An example of an IQY attachment from the current campaign follows.
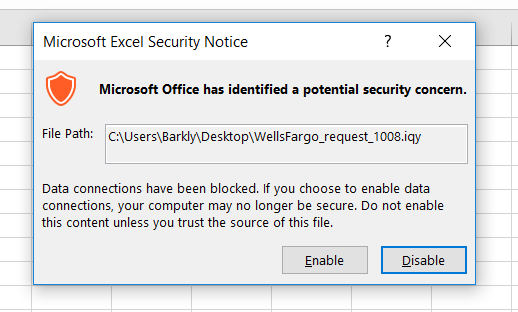
Fortunately, opening this file type spawns two warning messages that the recipient has to agree to before the attachment will open and download the RAT. Hopefully, that should be enough to prevent this exploit from launching, but often busy workers will just click through without a careful reading of the warnings. This is the first warning.
If the recipient clicks “Enable” on the first one, then this warning appears.
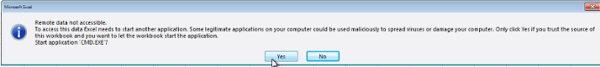
“Remote data is not accessible.
To access this data Excel needs to start another application. Some legitimate applications on your computer could be used maliciously to spread viruses or damage your computer. Only click Yes if you trust the source of the workbook and you want to let the workbook start the application.
Start application “CMD.EXE”?”
Of course clicking Yes will install the RAT.
This campaign also used Microsoft Publisher files with macros enabled. We have warned about the return of MS Office macro exploits before (Word and Excel Macro Viruses Are Back). Here again, the recipient has to enable macros for the exploit to run, and receives similar warning messages.
These emails appear to be sales requests, “IMPORTANT Documents” arriving from a major bank, bank related PDF attachments, password-protected ZIP files, fake invoices arriving as a Word .doc attachment, payment advice, and payment notifications. For a complete look at the phishing email samples see the Barkly article linked below. Blocking these types of attacks can be accomplished through Group Policy, and the process is outlined in the Barkly article.
If you are the cybersecurity officer at a bank, having a quick cybersecurity awareness lunch and learn session with slides showing the examples from the Barkly post would be another good idea. This attack variant is appearing more frequently, and evolving into new forms. Showing your staff examples of the warning messages and email types to guard against is important, too.
More information:
- FlawedAmmyy RAT
- Barkly blog – Necurs Botnet – good technical readout
- TechRepublic – Financial phishing attacks
- Word and Excel Macro Viruses Are Back
Share
AUG




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com